Embezzlement & Inventory Management
Optimize your Embezzlement & Inventory Management processes. Manage the entire lifecycle of the assets you use in IT service management processes end-to-end. Increase operational efficiency, reduce costs and ensure sustainability in your IT infrastructure for uninterrupted service!
Optimize your Embezzlement & Inventory Management processes. Manage the entire lifecycle of the assets you use in IT service management processes end-to-end. Increase operational efficiency, reduce costs and ensure sustainability in your IT infrastructure for uninterrupted service!
Benefits of the Embezzlement & Inventory Management Module

Thanks to inventory & embezzlement management, all physical and virtual assets in the IT infrastructure become visible. This transparency offers a great advantage in terms of rapid decision-making and clarification of responsibilities. In addition, knowing which equipment is used where facilitates rapid response to potential failures and optimizes resource utilization.

Unnecessary purchases are prevented and existing resources are used in the most efficient way. Prevents waste, especially in consumables management. Since the depreciation process of assets is clearly monitored, budget planning is done more accurately and return on investment is maximized.

Thanks to processes such as license term tracking and property registration, the organization is ready for external audits or internal control processes. Embezzlement management is one of the basic building blocks of this process. Being able to provide accurate and complete data during audits saves both time and prestige in terms of compliance with regulations.

Faulty equipment is quickly identified and maintenance planning is done without delay. This prevents service interruptions and increases user satisfaction. In addition, proactive maintenance strategies can be developed thanks to past failure records.
With inventory management software, manual tracking of processes is eliminated and inventory tracking is digitized by updating data in real time. In this way, organizations run error-free and scalable operations by creating an automationsupported infrastructure. It also eliminates information silos by integrating with internal systems.
Thanks to inventory & embezzlement management, all physical and virtual assets in the IT infrastructure become visible. This transparency offers a great advantage in terms of rapid decision-making and clarification of responsibilities. In addition, knowing which equipment is used where facilitates rapid response to potential failures and optimizes resource utilization.
Unnecessary purchases are prevented and existing resources are used in the most efficient way. Prevents waste, especially in consumables management. Since the depreciation process of assets is clearly monitored, budget planning is done more accurately and return on investment is maximized.
Thanks to processes such as license term tracking and property registration, the organization is ready for external audits or internal control processes. Embezzlement management is one of the basic building blocks of this process. Being able to provide accurate and complete data during audits saves both time and prestige in terms of compliance with regulations.
Faulty equipment is quickly identified and maintenance planning is done without delay. This prevents service interruptions and increases user satisfaction. In addition, proactive maintenance strategies can be developed thanks to past failure records.
With inventory management software, manual tracking of processes is eliminated and inventory tracking is digitized by updating data in real time. In this way, organizations run error-free and scalable operations by creating an automationsupported infrastructure. It also eliminates information silos by integrating with internal systems.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
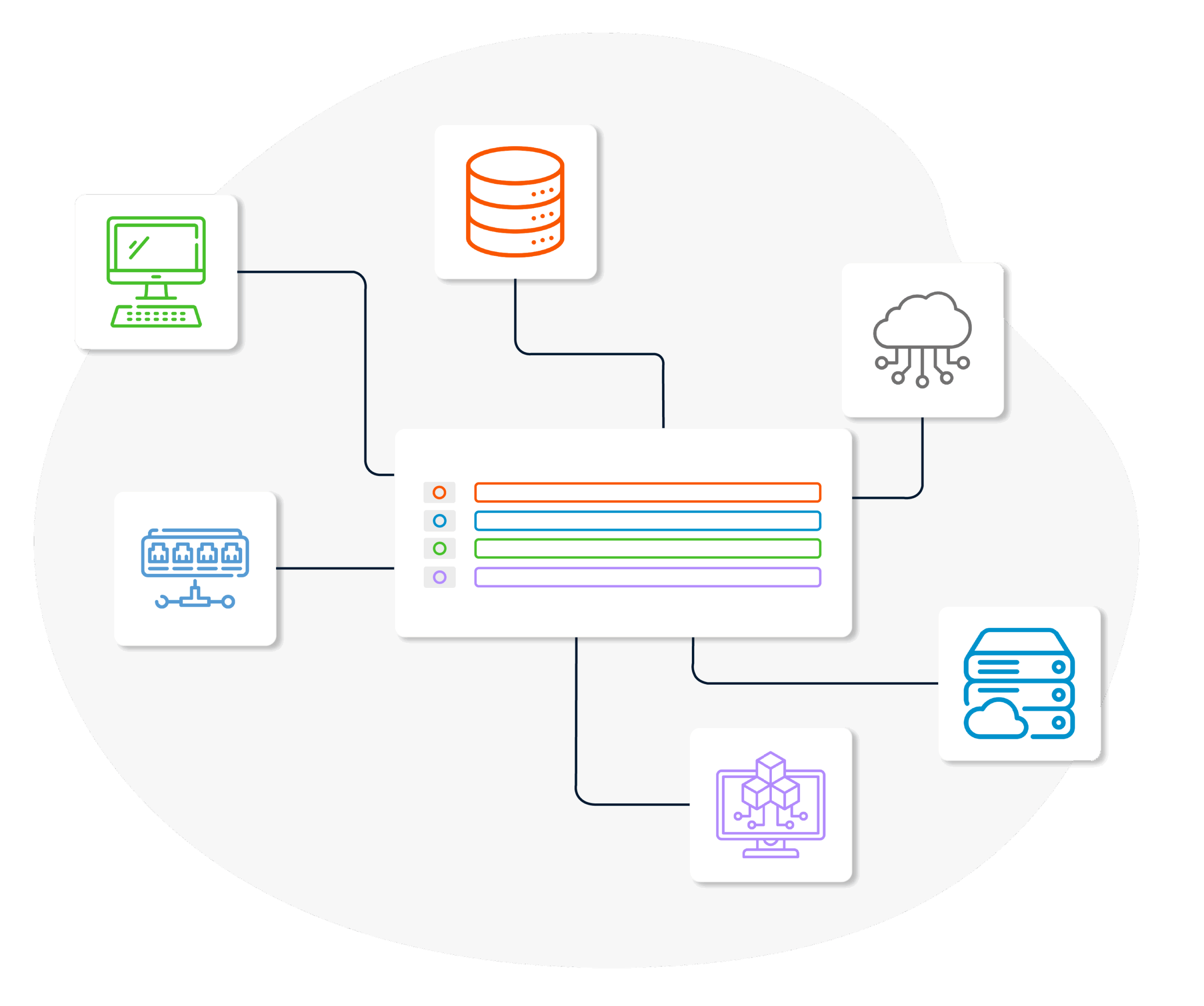
All devices (servers, desktops, mobiles, network hardware) and virtual assets are centrally registered in a single system. Thus, access to data becomes easier. This centralized structure enables the organization to monitor all IT assets from a single point and make decisions faster.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
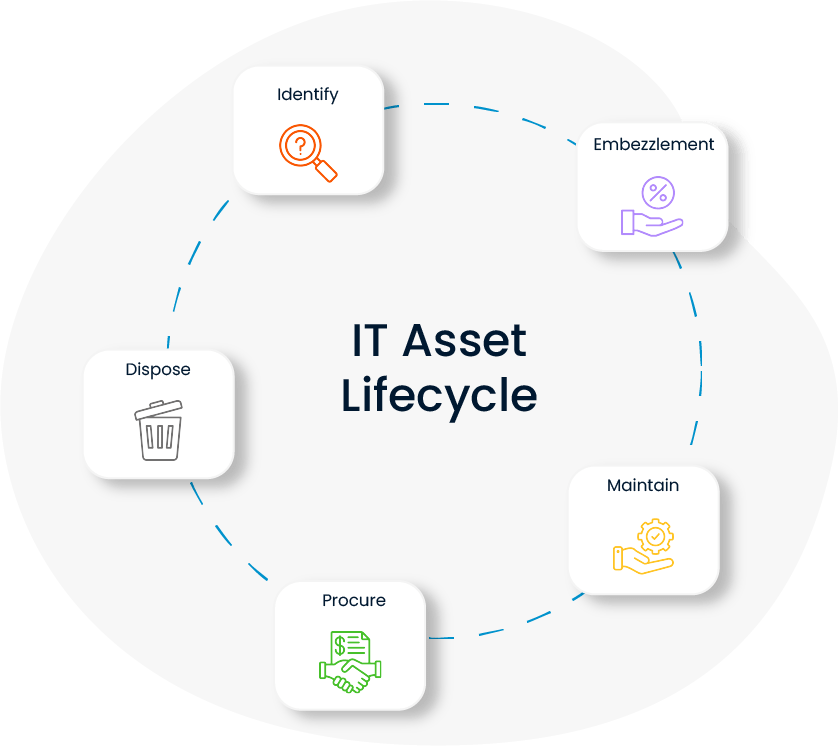
Each stage of the IT asset lifecycle (purchase, use, maintenance, disposal) is systematically monitored and optimized. This extends the life of the equipment and increases the return on investment. In addition, this management enables maintenance schedules to be made more strategically.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
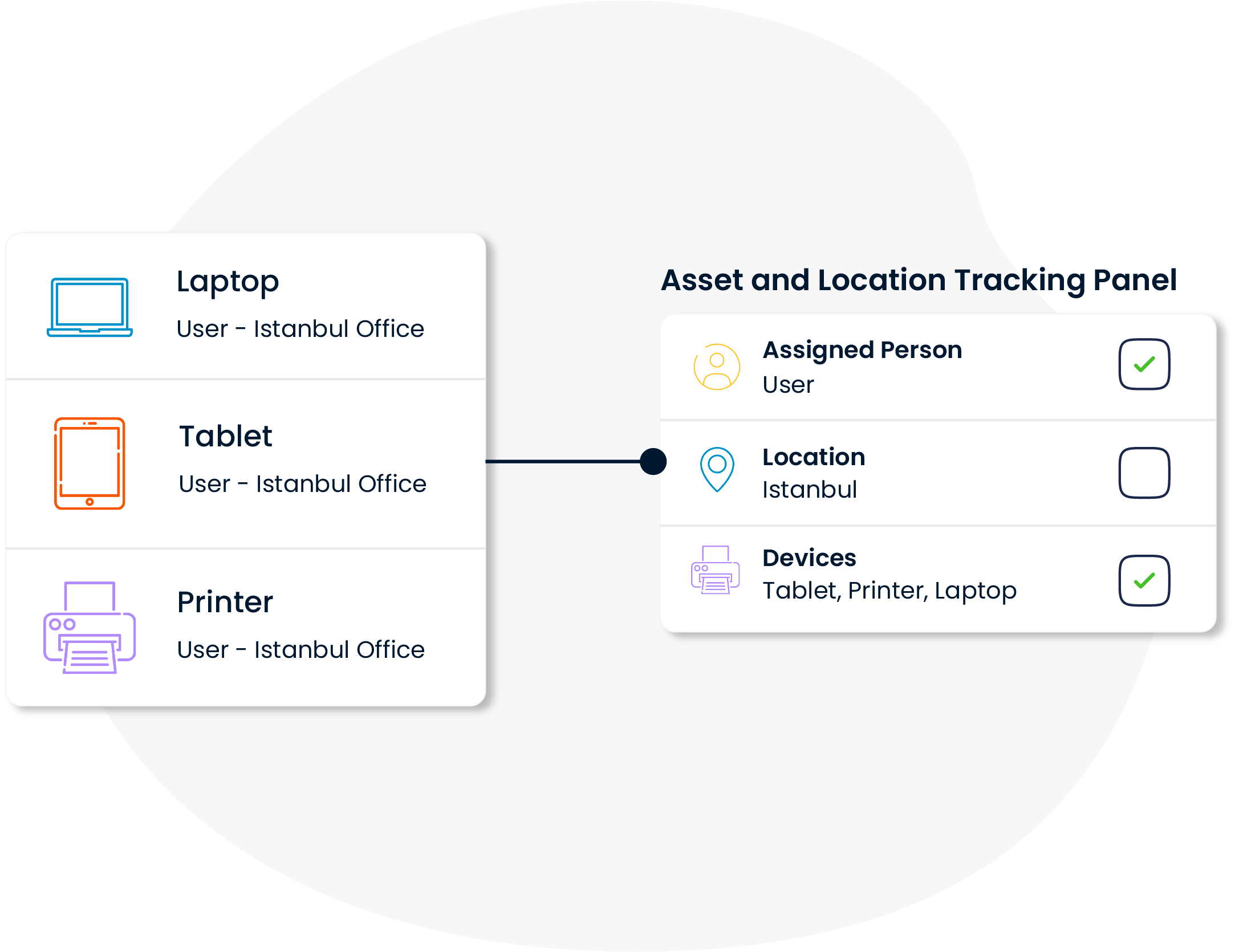
Information such as where each device is located and who is using it is kept up-to-date on the system. Embezzlement management is the basis of security and traceability in this context. This speeds up the detection of lost or stolen equipment and minimizes security gaps.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
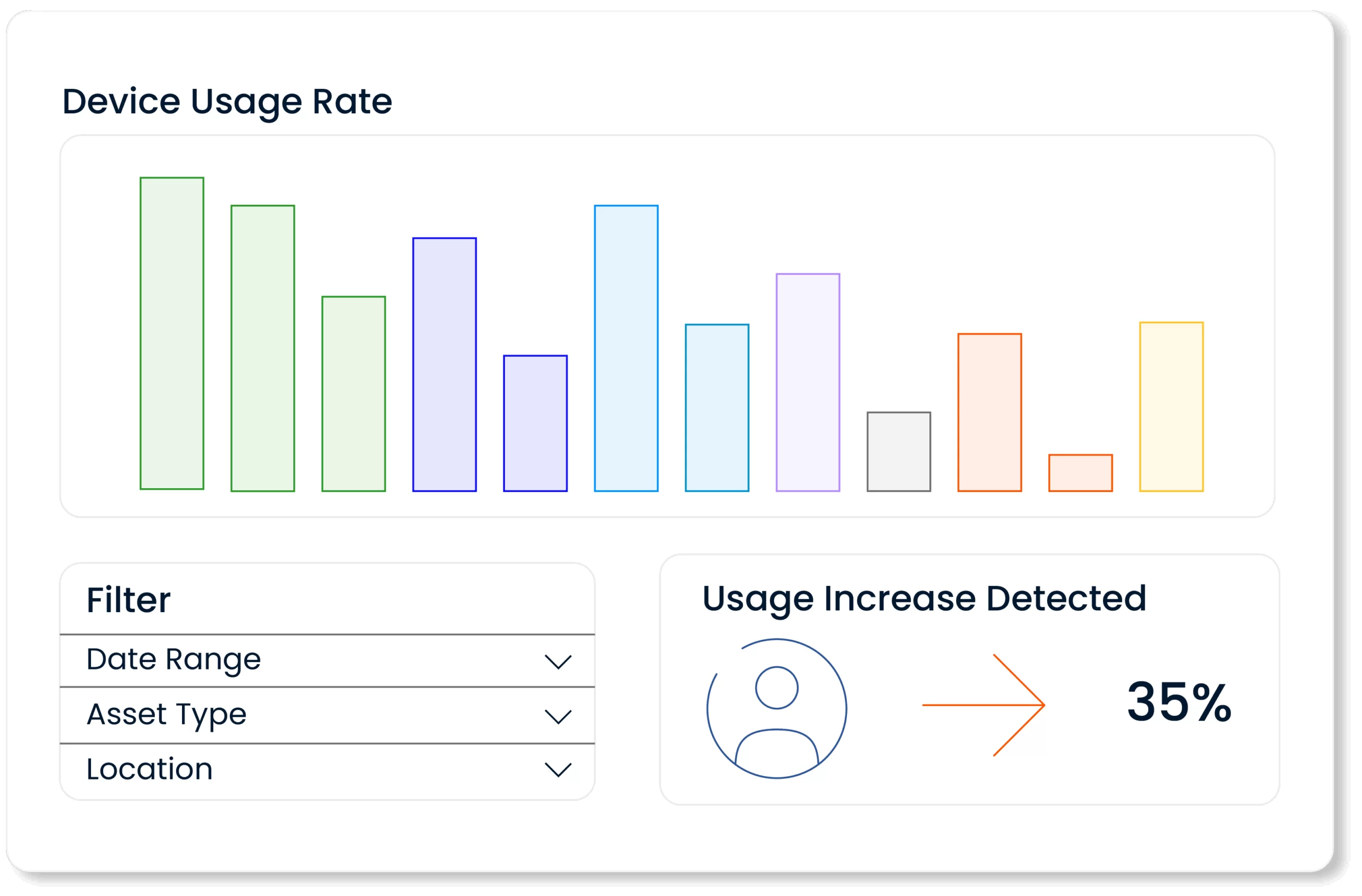
Inventory & embezzlement management systems provide managers with strategic insights by instantly reporting utilization rates, asset status and maintenance needs. With visual dashboards and filterable reports, complex data sets can be easily analyzed. This enables managers and teams to take the right action at the right time.

Thanks to inventory & embezzlement management, all physical and virtual assets in the IT infrastructure become visible. This transparency offers a great advantage in terms of rapid decision-making and clarification of responsibilities. In addition, knowing which equipment is used where facilitates rapid response to potential failures and optimizes resource utilization.

Unnecessary purchases are prevented and existing resources are used in the most efficient way. Prevents waste, especially in consumables management. Since the depreciation process of assets is clearly monitored, budget planning is done more accurately and return on investment is maximized.

Thanks to processes such as license term tracking and property registration, the organization is ready for external audits or internal control processes. Embezzlement management is one of the basic building blocks of this process. Being able to provide accurate and complete data during audits saves both time and prestige in terms of compliance with regulations.

Faulty equipment is quickly identified and maintenance planning is done without delay. This prevents service interruptions and increases user satisfaction. In addition, proactive maintenance strategies can be developed thanks to past failure records.

With inventory management software, manual tracking of processes is eliminated and inventory tracking is digitized by updating data in real time. In this way, organizations run error-free and scalable operations by creating an automationsupported infrastructure. It also eliminates information silos by integrating with internal systems.
Features of the Embezzlement & Inventory Management Module

Central Asset Registration System
Life Cycle Oriented Management

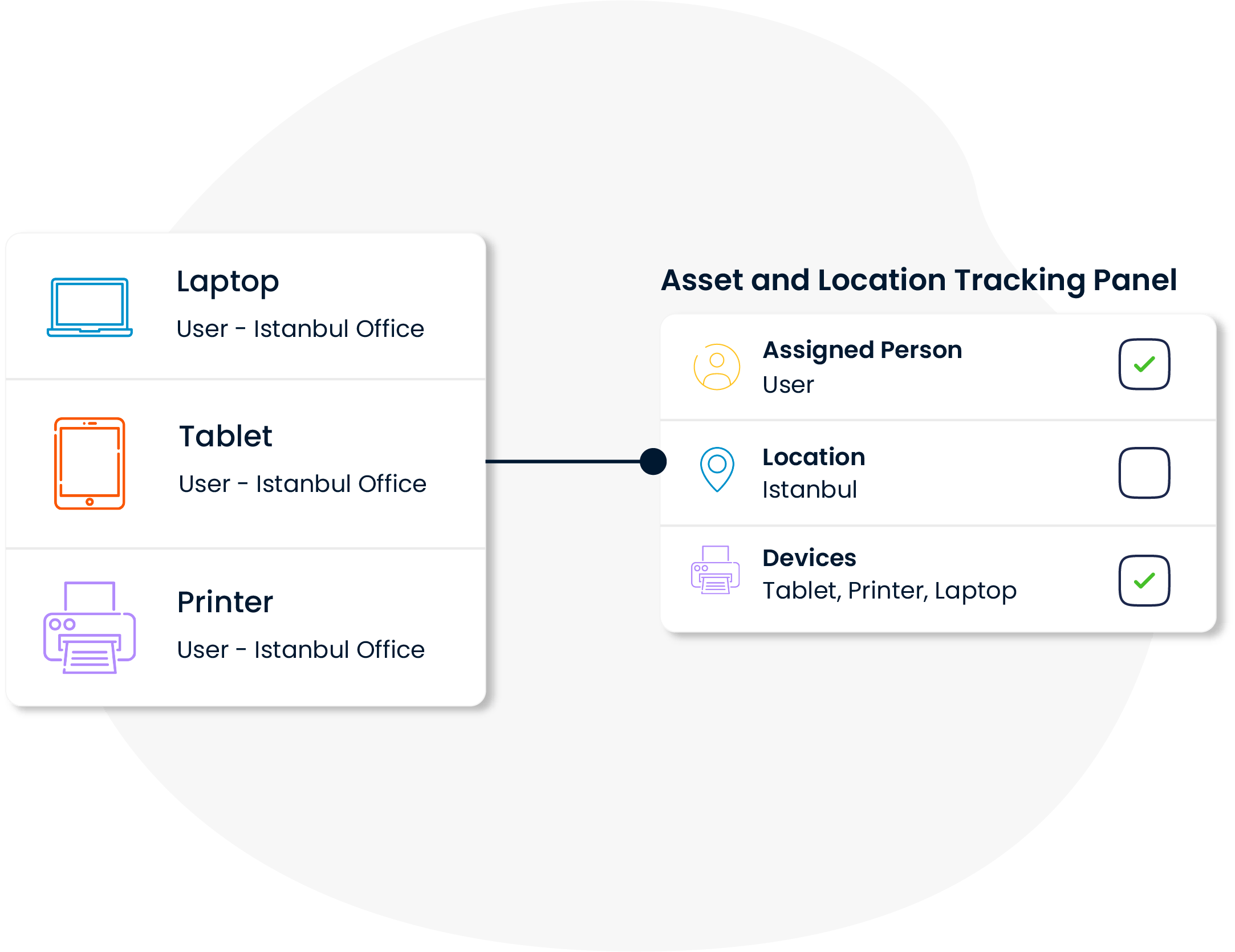
Location and Property Information Tracking
Dynamic Reporting and Inventory Status




Frequently Asked Questions (FAQ)
Inventory management enables centralized control of devices and assets to ensure the sustainability of IT operations. This process enables early detection of system vulnerabilities, reduces costs and prevents service interruptions. It also provides management with a strong decision support infrastructure in critical areas such as audit, maintenance and budgeting.
Physical assets (servers, laptops, printers) and virtual resources (virtual machines, containers) should be integrated into this process. At the same time, consumables such as licenses, software assets and consumables should also be tracked under inventory. This comprehensive approach provides complete visibility and enables effective management of all resources.
No, it is not. Inventory management directly affects the decision-making and planning processes of many different business units such as human resources, finance and operations. Issues such as embezzlement processes, license usage or equipment requests require the entire organization to work in coordination.
Thanks to accurate inventory tracking, unnecessary investments are avoided, maintenance costs become predictable and budgeting is done with more realistic data. In particular, depreciation calculations and life cycle analyses provide valuable insights for accurate financial planning. In this way, organizations can build not only today, but also their long-term investments on a more solid foundation.
With up-to-date inventory information, security vulnerabilities can be identified and which devices need to be updated can be determined. Security risk is minimized by removing out-of-use or out-of-support devices from the system. In addition, unauthorized access can be prevented and security policies can be implemented more effectively thanks to location and ownership tracking.
If You Have Any Other Questions, Contact Us!
Inventory management enables centralized control of devices and assets to ensure the sustainability of IT operations. This process enables early detection of system vulnerabilities, reduces costs and prevents service interruptions. It also provides management with a strong decision support infrastructure in critical areas such as audit, maintenance and budgeting.
Physical assets (servers, laptops, printers) and virtual resources (virtual machines, containers) should be integrated into this process. At the same time, consumables such as licenses, software assets and consumables should also be tracked under inventory. This comprehensive approach provides complete visibility and enables effective management of all resources.
No, it is not. Inventory management directly affects the decision-making and planning processes of many different business units such as human resources, finance and operations. Issues such as embezzlement processes, license usage or equipment requests require the entire organization to work in coordination.
Thanks to accurate inventory tracking, unnecessary investments are avoided, maintenance costs become predictable and budgeting is done with more realistic data. In particular, depreciation calculations and life cycle analyses provide valuable insights for accurate financial planning. In this way, organizations can build not only today, but also their long-term investments on a more solid foundation.
With up-to-date inventory information, security vulnerabilities can be identified and which devices need to be updated can be determined. Security risk is minimized by removing out-of-use or out-of-support devices from the system. In addition, unauthorized access can be prevented and security policies can be implemented more effectively thanks to location and ownership tracking.
