Configuration Management Database
Strengthen your configuration management processes by centrally managing all data related to hardware and software components. Analyze relationships between Configuration Items (CIs) to make your CMDB activities more transparent, secure, and effective.
Strengthen your configuration management processes by centrally managing all data related to hardware and software components. Analyze relationships between Configuration Items (CIs) to make your CMDB activities more transparent, secure, and effective.
Benefits of the Configuration Management Database
By defining all hardware and software components as Configuration Items (CIs), organizations can gain a detailed view of their IT infrastructure. This visibility makes it easier to identify potential bottlenecks in complex systems and supports strategic planning.

With Configuration Management, the impact of a change on a single component can be analyzed across the entire system in advance. This helps minimize unplanned outages, data loss, and misconfigurations.

By integrating with inventory and monitoring systems, the CMDB minimizes manual data entry. This eliminates issues like outdated records, missing information, and inconsistencies.

With Configuration Management, past changes, relationships, and access permissions are thoroughly recorded. These records provide reliable information for external audits and help improve internal controls.
By analyzing the cost, licensing, and usage status of CIs, resource allocation becomes more accurate. This is especially valuable for large organizations looking to optimize their IT budgets.
By defining all hardware and software components as Configuration Items (CIs), organizations can gain a detailed view of their IT infrastructure. This visibility makes it easier to identify potential bottlenecks in complex systems and supports strategic planning.
With Configuration Management, the impact of a change on a single component can be analyzed across the entire system in advance. This helps minimize unplanned outages, data loss, and misconfigurations.
By integrating with inventory and monitoring systems, the CMDB minimizes manual data entry. This eliminates issues like outdated records, missing information, and inconsistencies.
With Configuration Management, past changes, relationships, and access permissions are thoroughly recorded. These records provide reliable information for external audits and help improve internal controls.
By analyzing the cost, licensing, and usage status of CIs, resource allocation becomes more accurate. This is especially valuable for large organizations looking to optimize their IT budgets.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
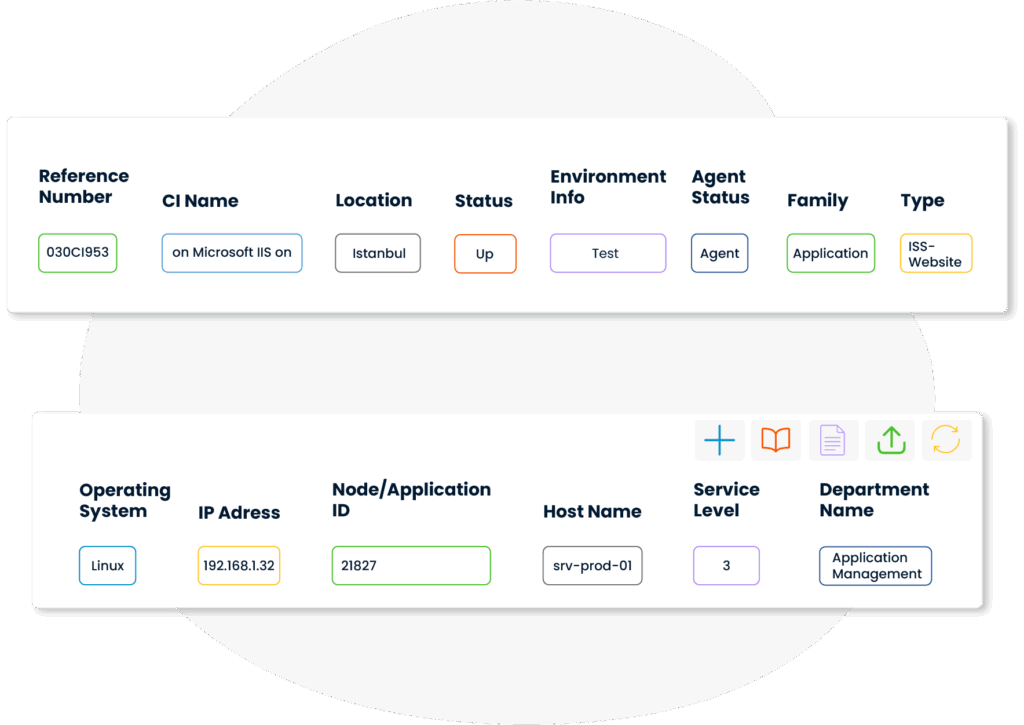
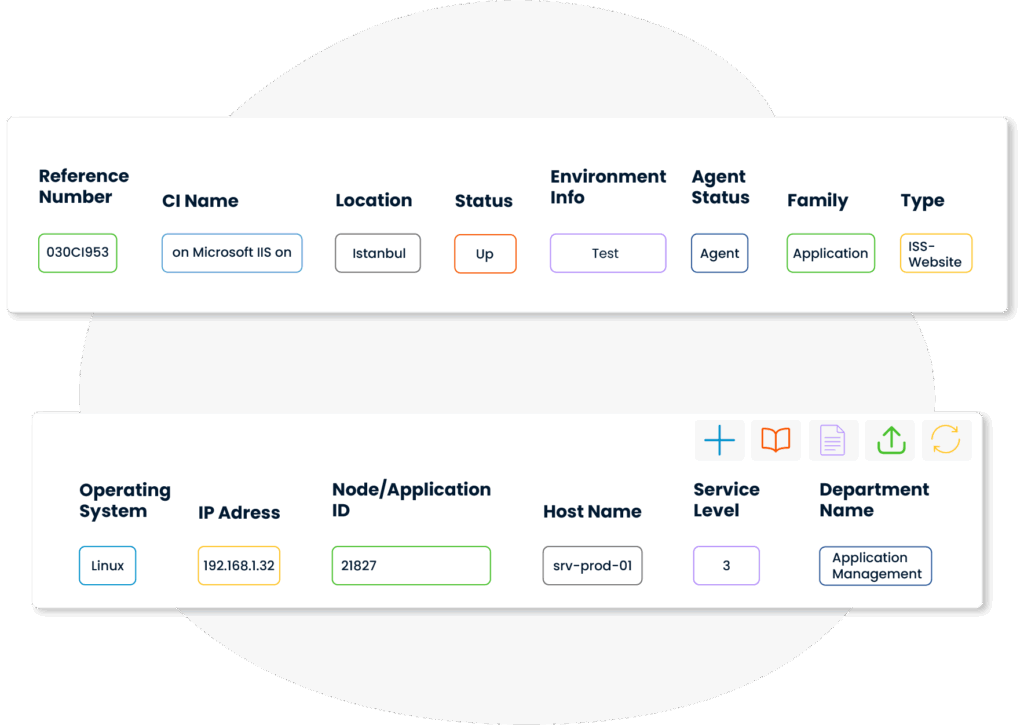
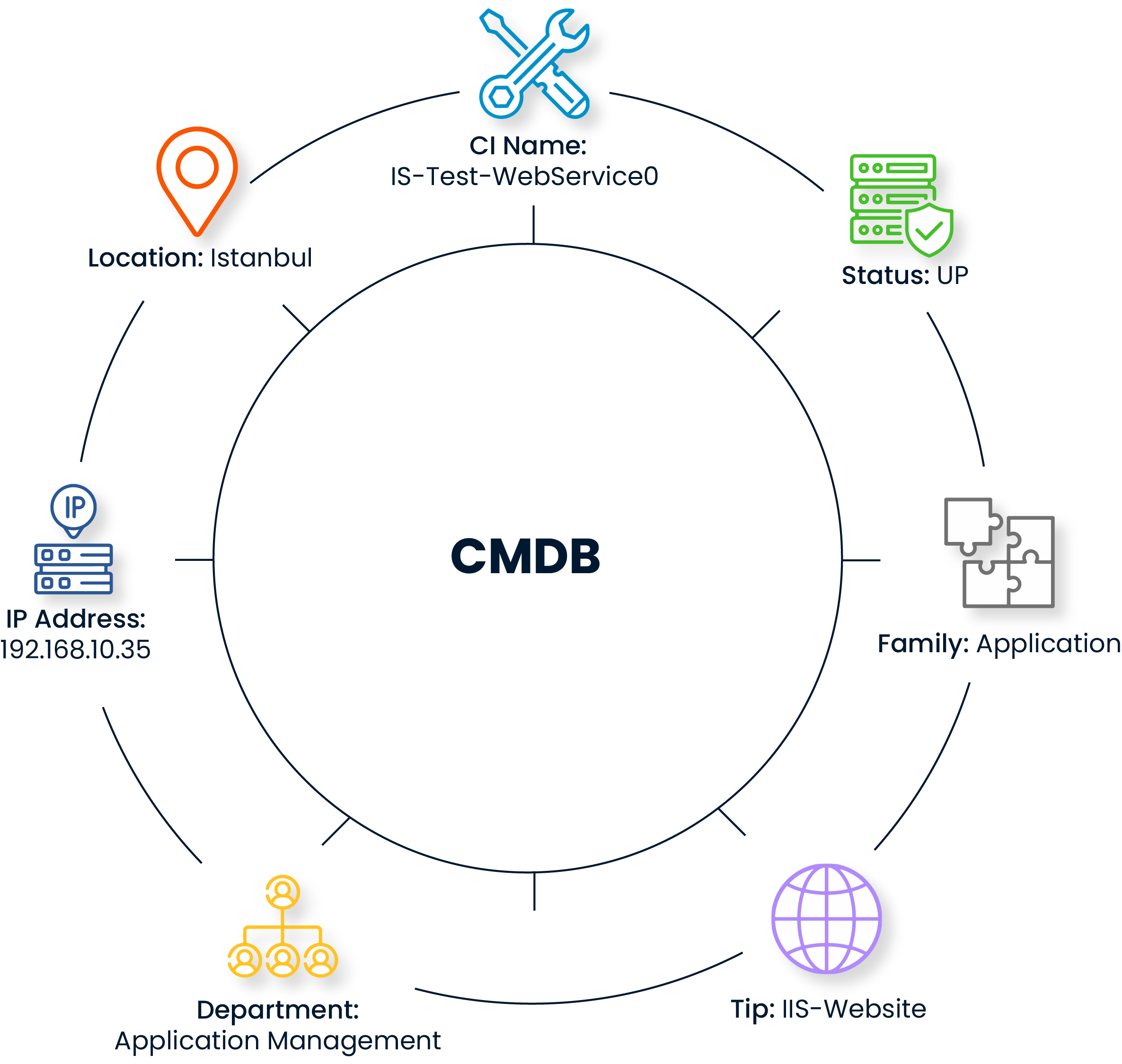
Each component is recorded as a CI—whether it' s hardware, software, or a service. This ensures full control over all infrastructure elements, leaving no undocumented assets behind.
With the help of a CMDB, technical, locational, and financial information related to each CI can be monitored centrally. This structure provides a solid data foundation for IT configuration management processes.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
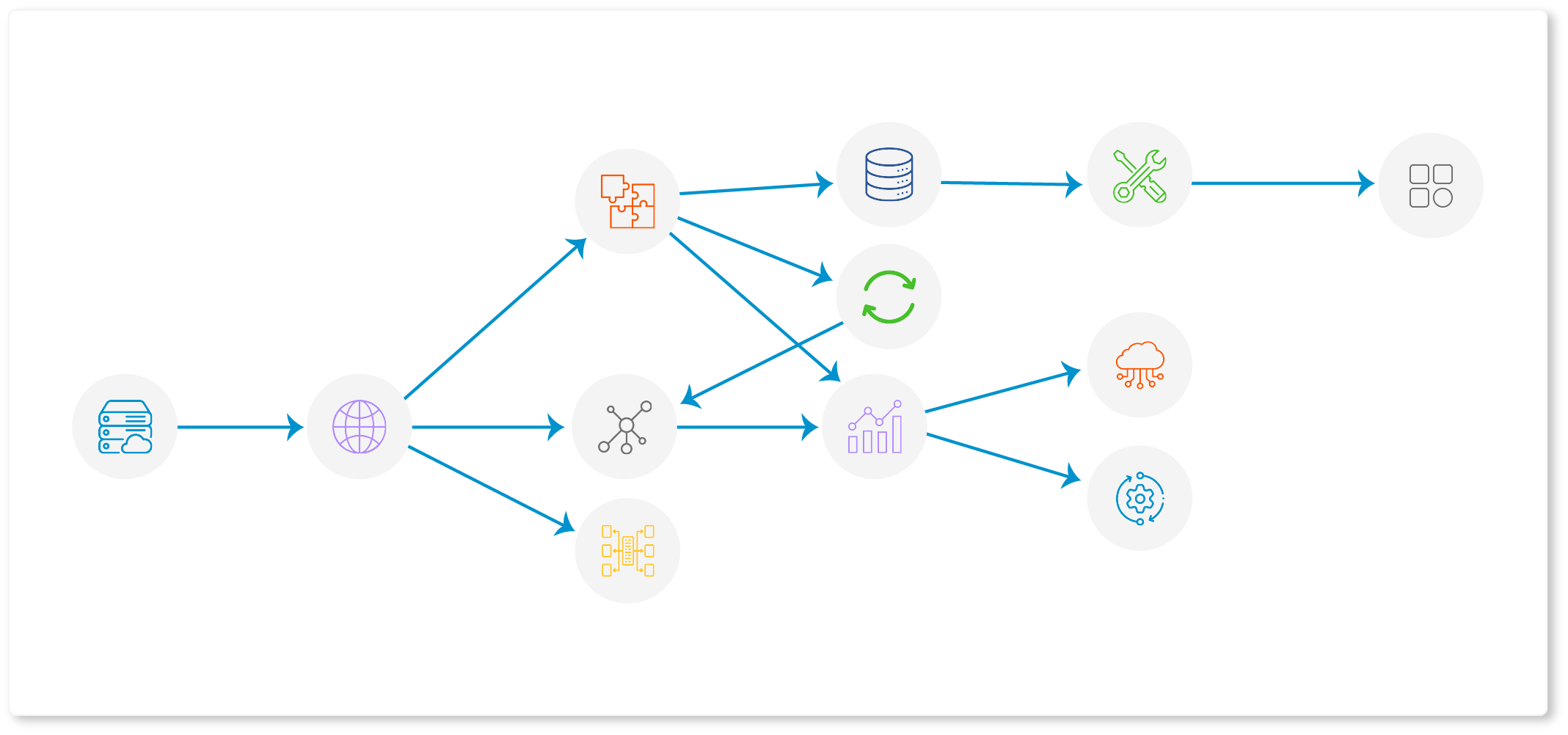
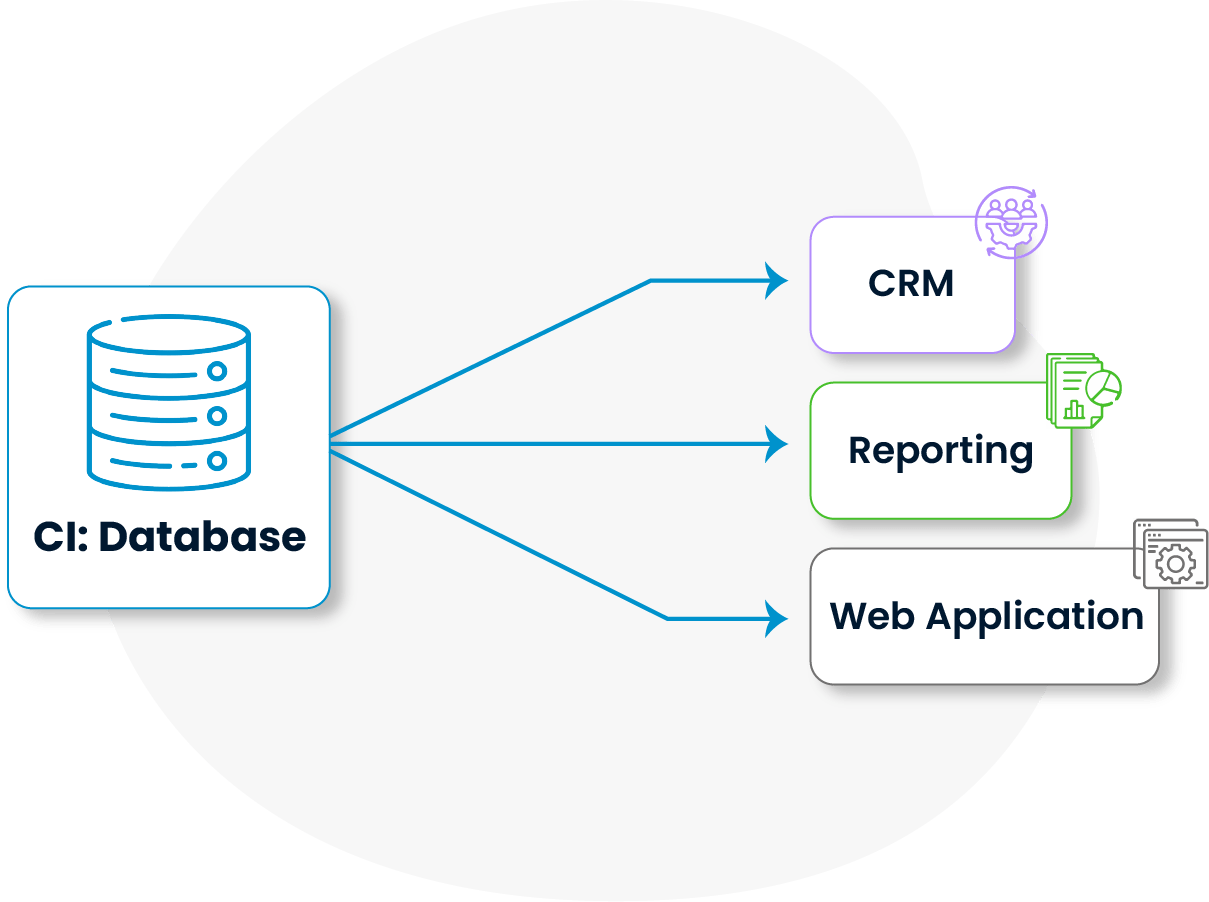
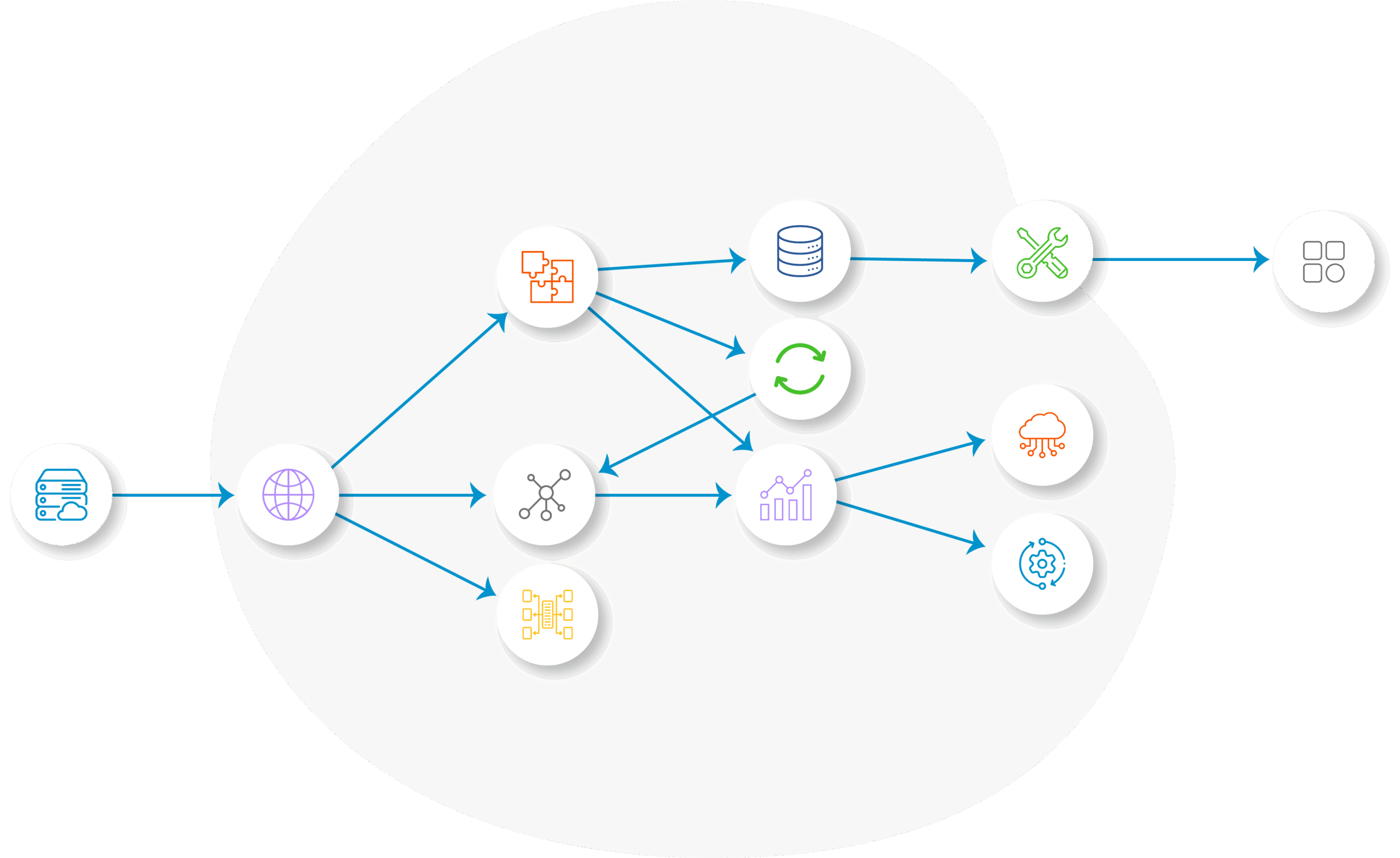
Relationships between CIs are visually mapped, accelerating decision-making during service impact analyses. Configuration management enables you to anticipate how applications, servers, and databases affect one another.
Dependency maps clearly visualize the potential impact area before planned maintenance or changes, ensuring better-informed planning.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
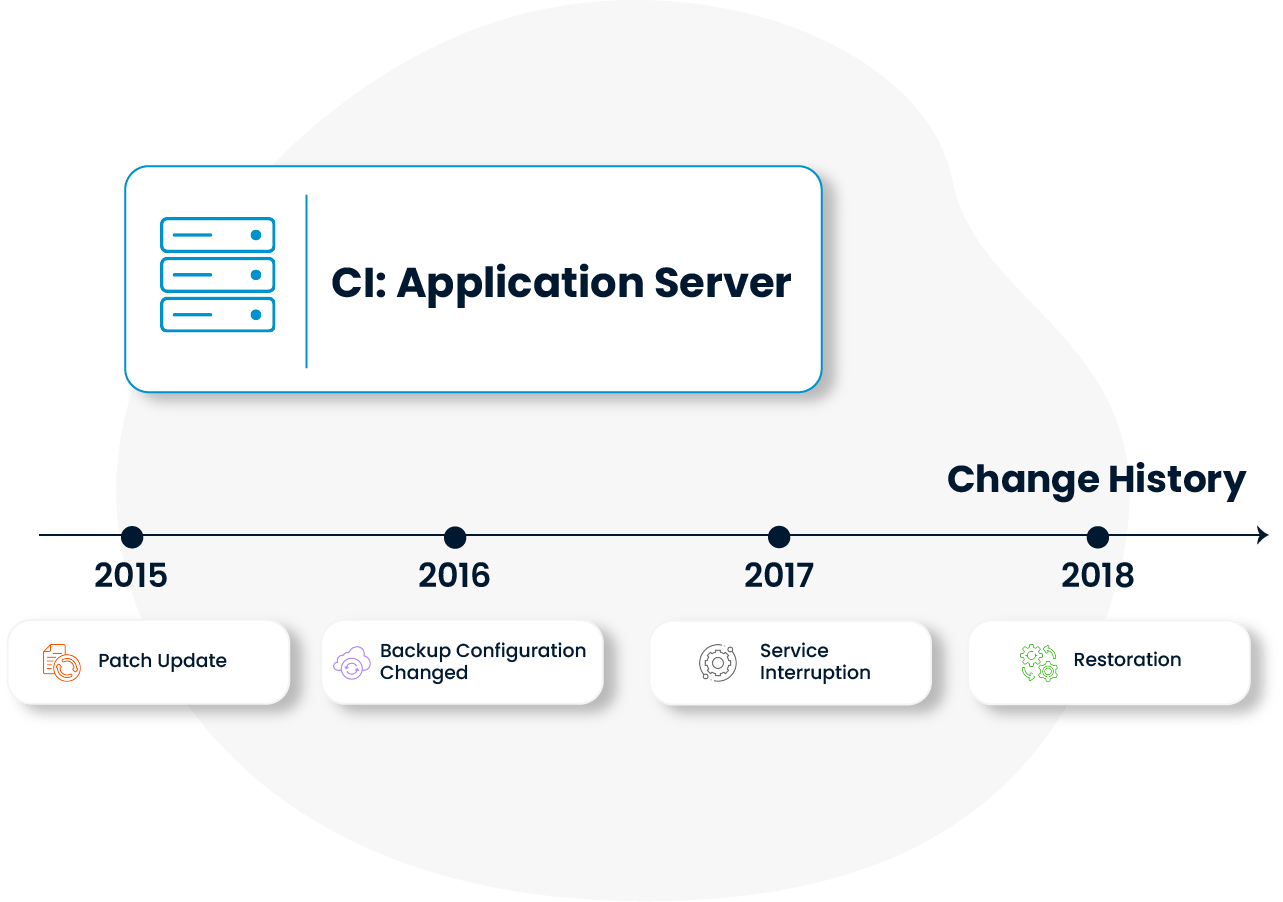
Every change made to a CI—what was changed, when, and how—is tracked in detail. This brings transparency and traceability to the configuration management process.
Change records support historical analysis and foster a culture of continuous improvement. They also provide critical data for root cause analysis of unexpected issues in the IT infrastructure.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
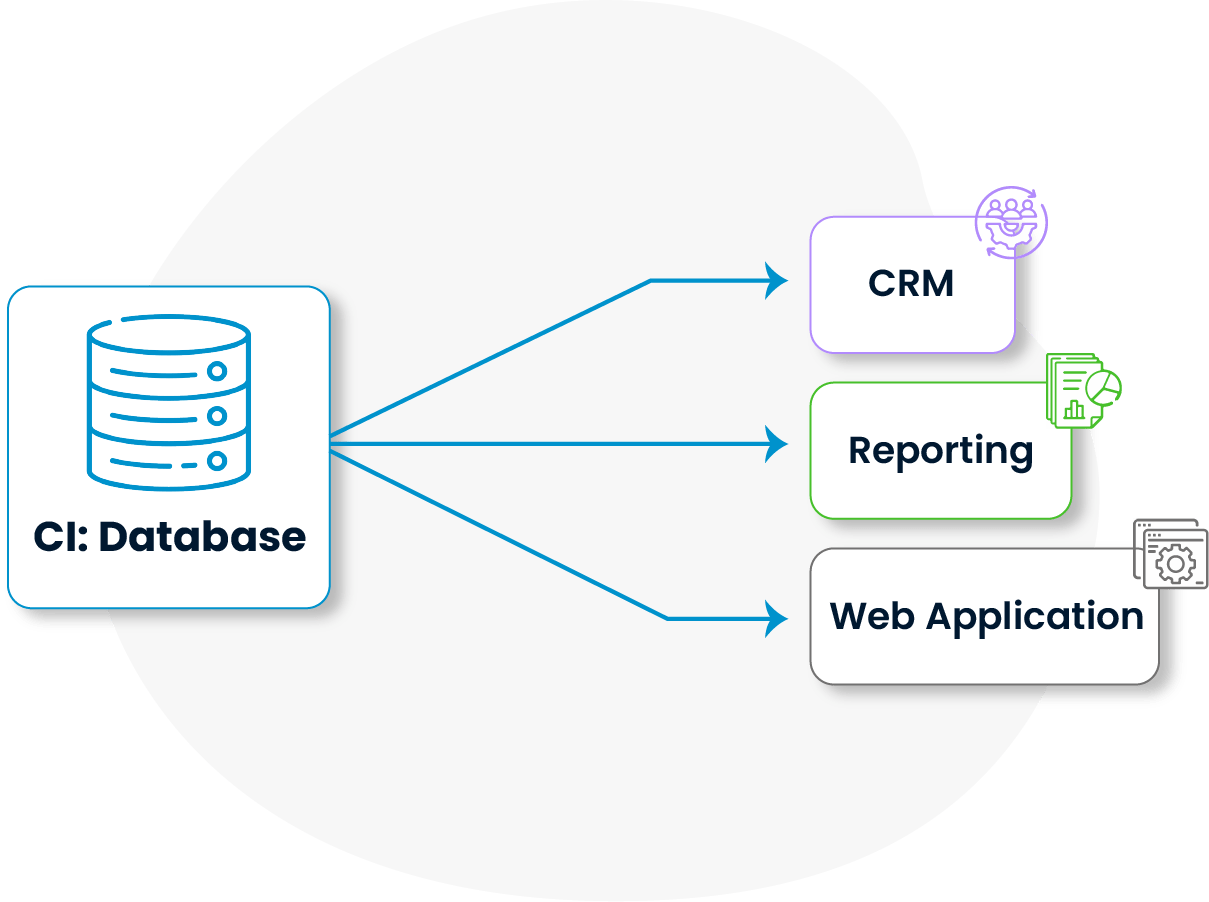
Any change to a CI is analyzed for its potential effects on other systems. This helps prevent unplanned outages and cascading failures. In environments where service interruptions pose a risk, such analysis enables the strategic use of the CMDB. With this level of foresight, IT configuration management becomes more proactive.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
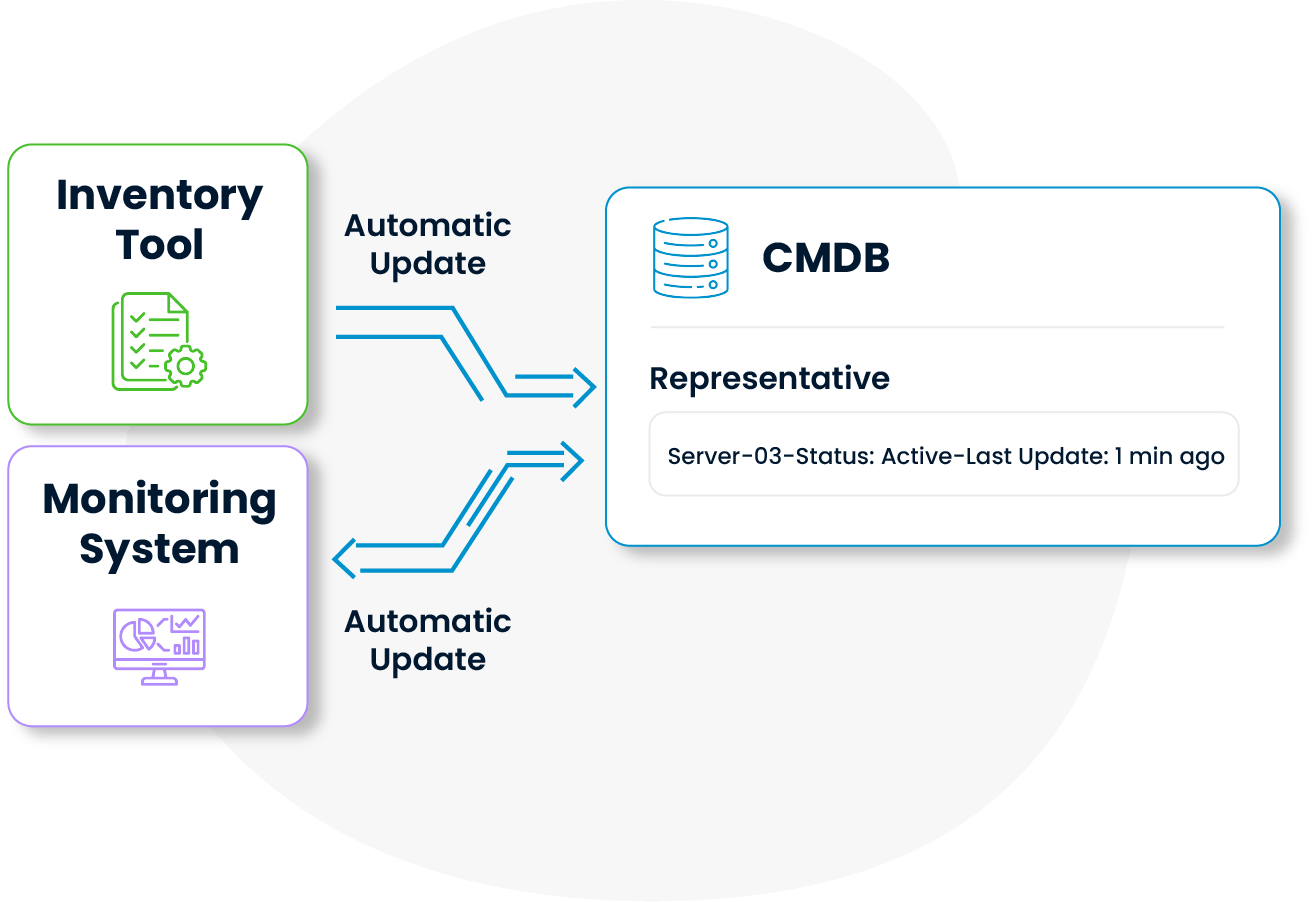
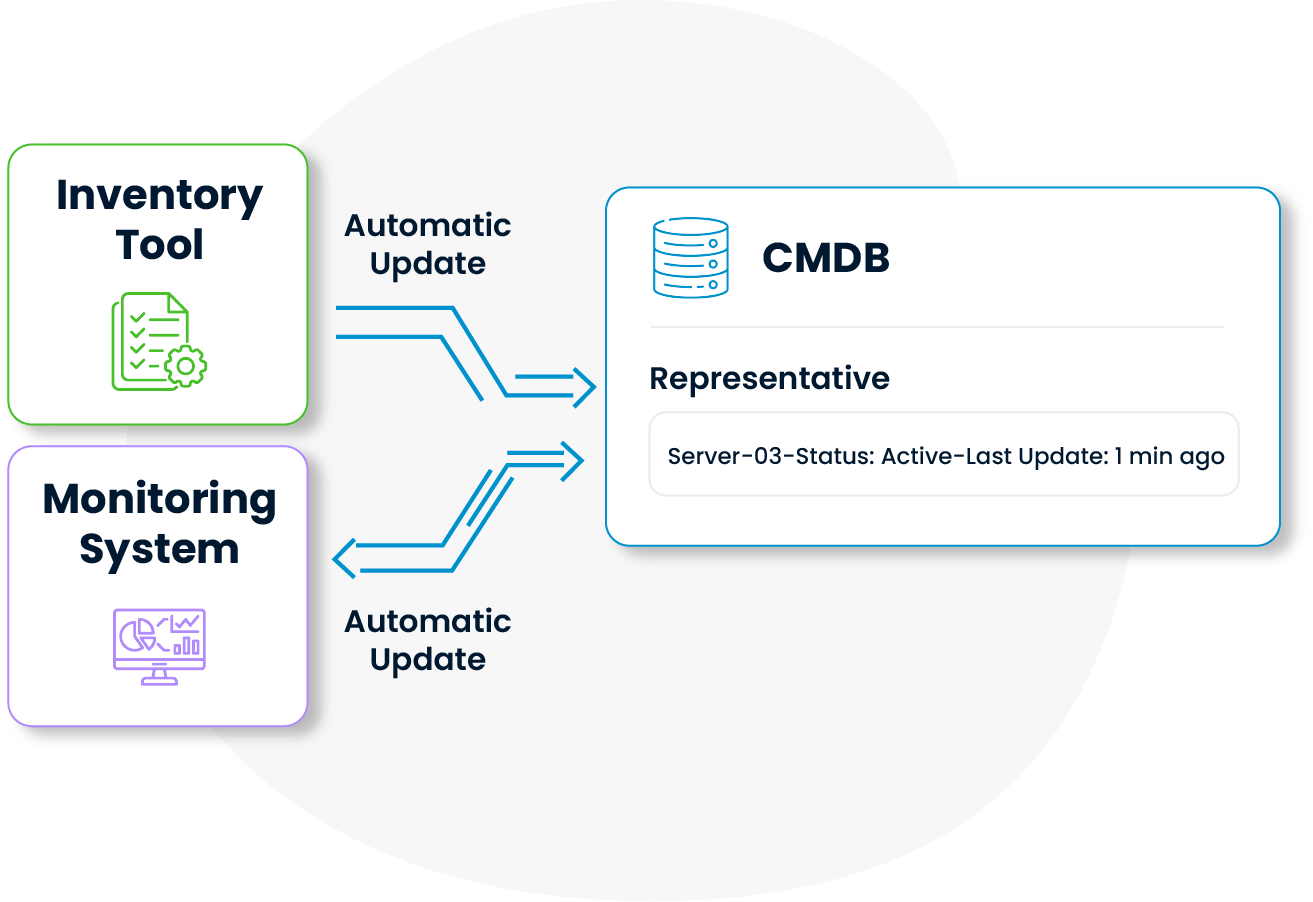
The CMDB automatically synchronizes with inventory management and monitoring tools to ensure data integrity. This eliminates the need for manual efforts to keep data up to date.
Configuration items are automatically aligned with real-time system changes, making configuration management processes more accurate with less human intervention.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
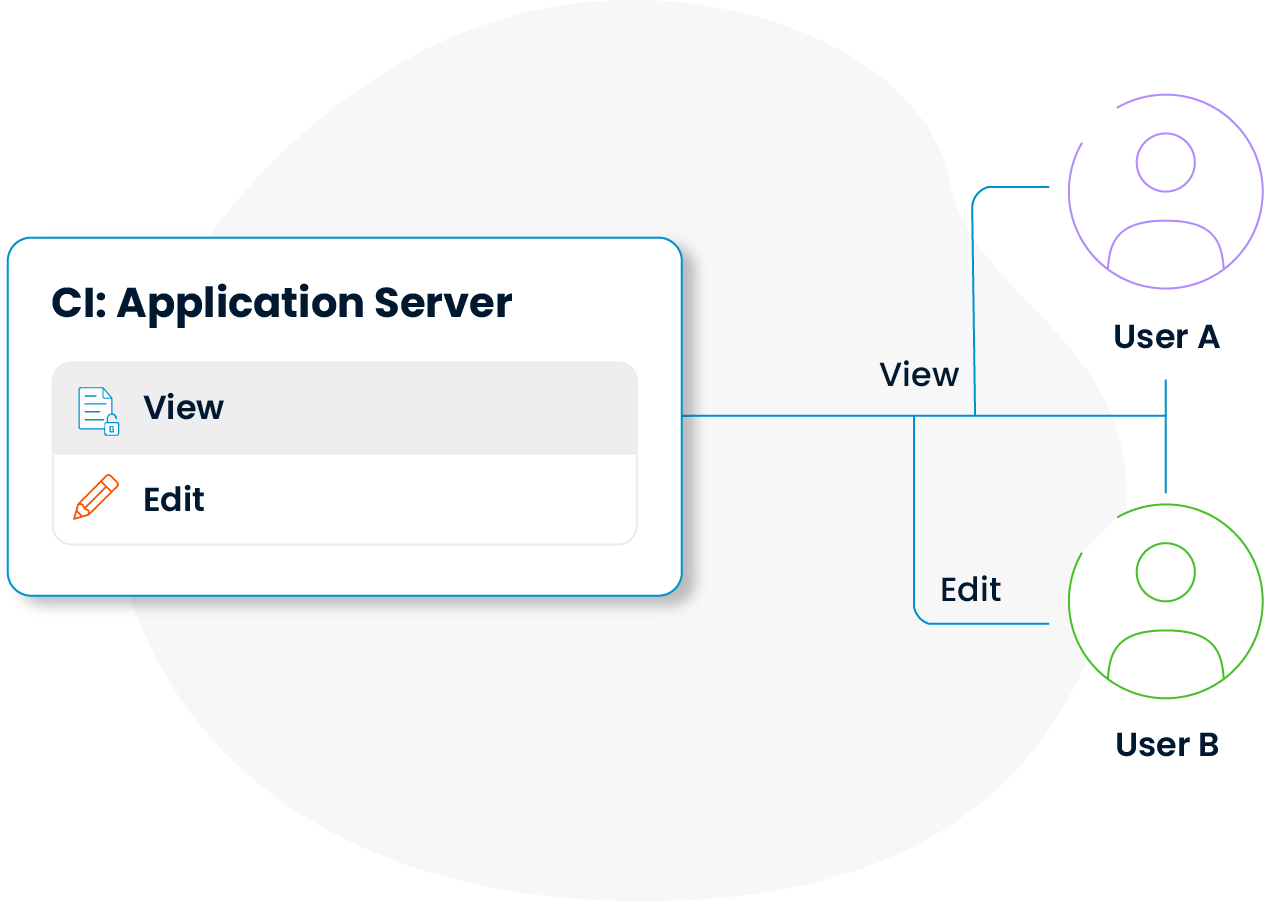
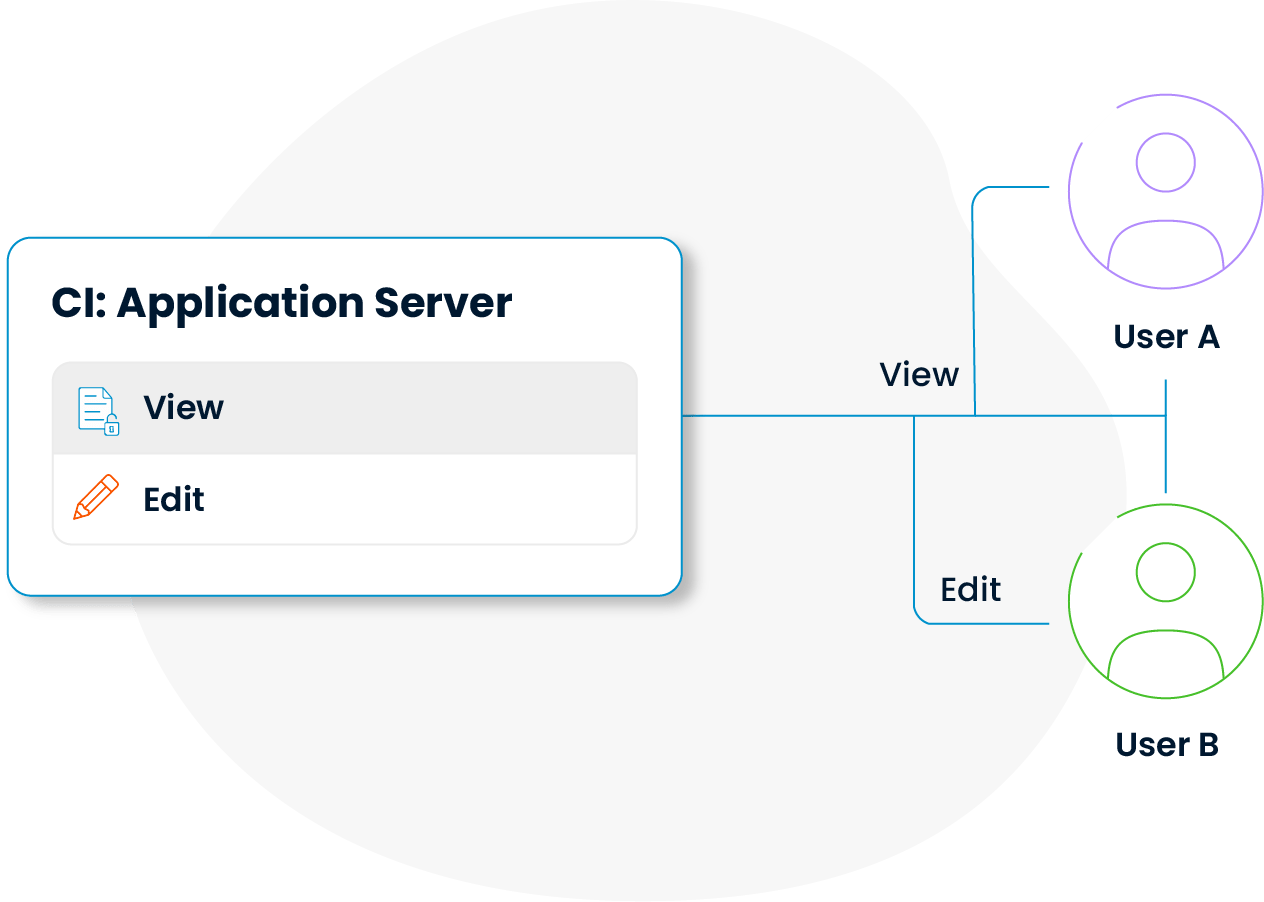
Clear rules define which users can access which data, ensuring both data security and clear responsibility allocation.
Access and edit permissions for CI information are integrated with corporate security policies. This way, configuration management balances security and transparency effectively.

By defining all hardware and software components as Configuration Items (CIs), organizations can gain a detailed view of their IT infrastructure. This visibility makes it easier to identify potential bottlenecks in complex systems and supports strategic planning.

With Configuration Management, the impact of a change on a single component can be analyzed across the entire system in advance. This helps minimize unplanned outages, data loss, and misconfigurations.

By integrating with inventory and monitoring systems, the CMDB minimizes manual data entry. This eliminates issues like outdated records, missing information, and inconsistencies.

With Configuration Management, past changes, relationships, and access permissions are thoroughly recorded. These records provide reliable information for external audits and help improve internal controls.

By analyzing the cost, licensing, and usage status of CIs, resource allocation becomes more accurate. This is especially valuable for large organizations looking to optimize their IT budgets.
Features of the Configuration Management Database

Configuration Item (CI) Definitions
Dependency Mapping


Change Tracking
Impact Analysis
Automatic Update Mechanism
Authorization and Access Control





Frequently Asked Questions (FAQ)
CMDB is a centralized database that records all components of an organization’s IT infrastructure and the relationships between them. When properly managed, it provides transparency in configuration management and increases control over the infrastructure.
Inventory management focuses only on tracking physical assets, while a CMDB defines both physical and virtual components and analyzes dependencies between them. This makes it a more comprehensive and relational structure.
Information such as hardware, software, network devices, services, and related metadata (location, ownership, licensing) are stored in the CMDB. Additionally, critical data like change history, relationships, and versioning are recorded.
If CMDB data is outdated, it can lead to incorrect analyses and risky decisions. Automatic synchronization keeps the database current, directly impacting the effectiveness of configuration management processes.
Through authorization structures, it controls who can access which CIs. Also, potential vulnerabilities caused by misconfigurations can be detected early to maintain system integrity.
No. SMEs also need configuration management processes due to their growing infrastructures and complex IT systems. Even small organizations can gain efficiency and risk reduction with a CMDB.
If You Have Any Other Questions, Contact Us!
A CMDB is a centralized database that records all components of an organization ‘ s IT infrastructure and the relationships between them. When properly managed, it provides transparency in configuration management and increases control over the infrastructure.
Inventory management focuses only on tracking physical assets, while a CMDB defines both physical and virtual components and analyzes dependencies between them. This makes it a more comprehensive and relational structure.
Information such as hardware, software, network devices, services, and related metadata (location, ownership, licensing) are stored in the CMDB. Additionally, critical data like change history, relationships, and versioning are recorded.
If CMDB data is outdated, it can lead to incorrect analyses and risky decisions. Automatic synchronization keeps the database current, directly impacting the effectiveness of configuration management processes.
Through authorization structures, it controls who can access which CIs. Also, potential vulnerabilities caused by misconfigurations can be detected early to maintain system integrity.
No. SMEs also need configuration management processes due to their growing infrastructures and complex IT systems. Even small organizations can gain efficiency and risk reduction with a CMDB.
