Risk Management
Detect threats that may occur on business processes and systems in your IT ecosystem early and minimize potential damages with risk management. Integrate the operational risk management approach into your entire IT infrastructure with effective control, analysis and prevention mechanisms!

Detect threats that may occur on business processes and systems in your IT ecosystem early and minimize potential damages with risk management. Integrate the operational risk management approach into your entire IT infrastructure with effective control, analysis and prevention mechanisms!
Benefits of the Risk Management Module

The purpose of Risk Management in IT services is to identify potential risks in advance, mitigate them with effective strategies and ensure uninterrupted continuity of services. Thus, organizations become more resilient in times of crisis and the integrity of the IT infrastructure is ensured.

An effective enterprise risk management approach in IT services supports financial stability by anticipating unexpected costs. Controlling risks in advance optimizes investment and operation costs.
Monitoring the risks identified with Risk Management in IT services and effective control mechanisms prevent IT services from being interrupted. This provides a strong advantage to organizations in terms of service security.
Risk documentation and IT service management processes make it easier for organizations to comply with regulations and audit requirements. This increases credibility in external audits.

Risk analyses guide managers in strategic decision-making processes. Risk-based assessments offer more sustainable results, especially in IT operations management projects.
The purpose of Risk Management in IT services is to identify potential risks in advance, mitigate them with effective strategies and ensure uninterrupted continuity of services. Thus, organizations become more resilient in times of crisis and the integrity of the IT infrastructure is ensured.
An effective enterprise risk management approach in IT services supports financial stability by anticipating unexpected costs. Controlling risks in advance optimizes investment and operation costs.
Monitoring the risks identified with Risk Management in IT services and effective control mechanisms prevent IT services from being interrupted. This provides a strong advantage to organizations in terms of service security.
Risk documentation and IT service management processes make it easier for organizations to comply with regulations and audit requirements. This increases credibility in external audits.
Risk analyses guide managers in strategic decision-making processes. Risk-based assessments offer more sustainable results, especially in IT operations management projects.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
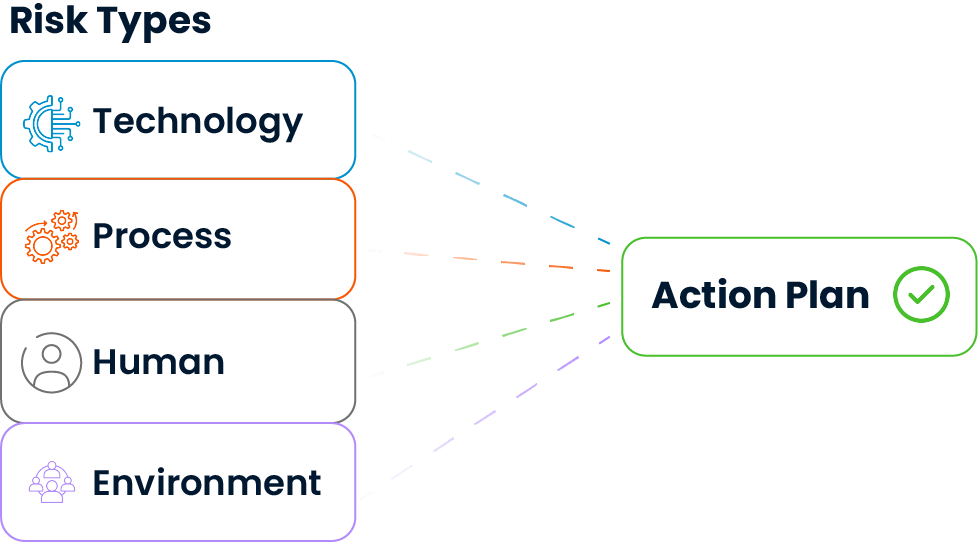
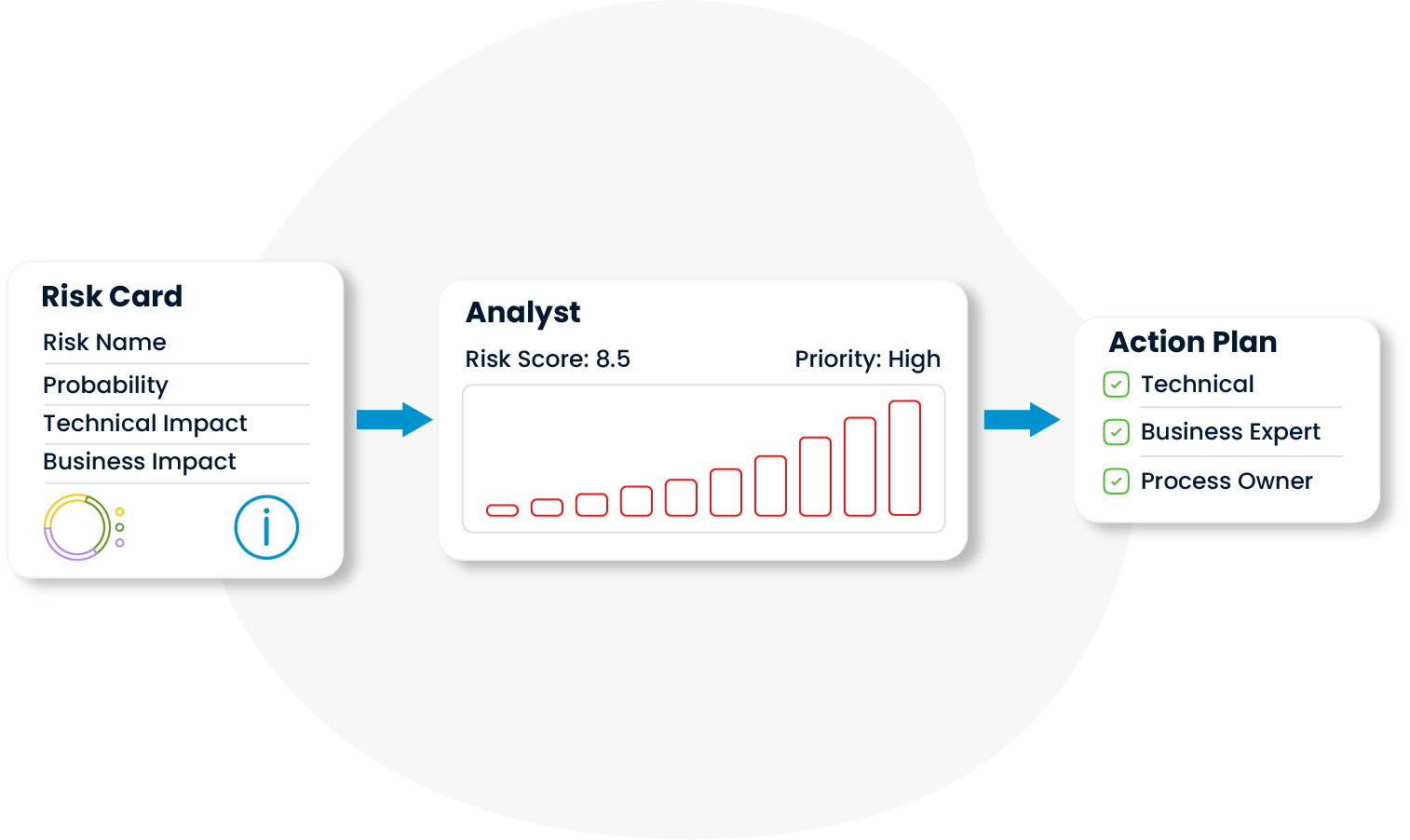
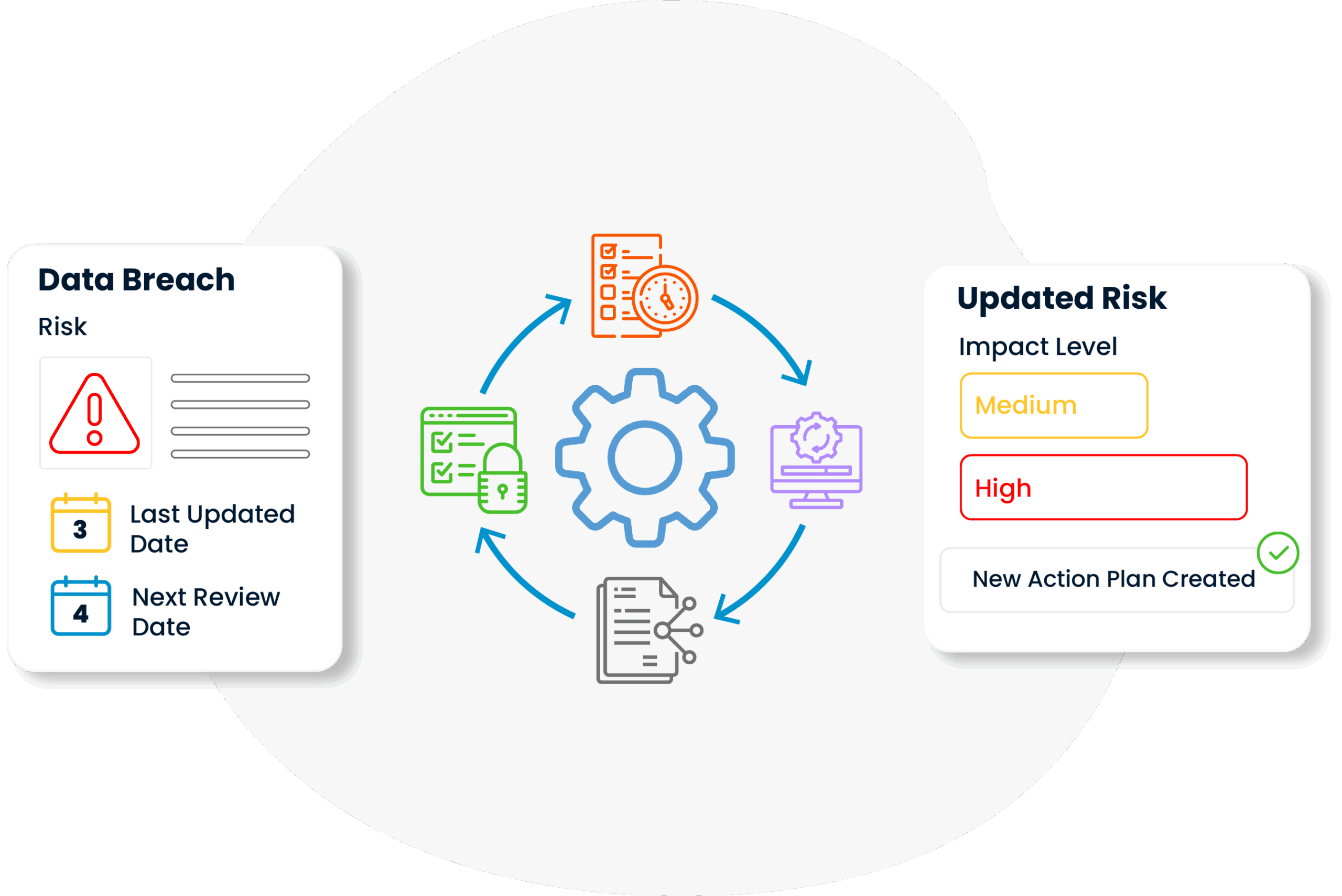
Potential threats are analyzed in detail under different categories such as technology, process, human resources and external environmental factors, not just superficial headings. This structured classification process enables the creation of target-oriented action plans appropriate to the source and nature of the risk.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
The probability and impact of risks are assessed not only from a technical perspective, but also in a multi-stakeholder structure, taking into account the operational objectives and strategic priorities of business units. Thus, the measures to be taken become meaningful and applicable in terms of business as well as technical validity.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
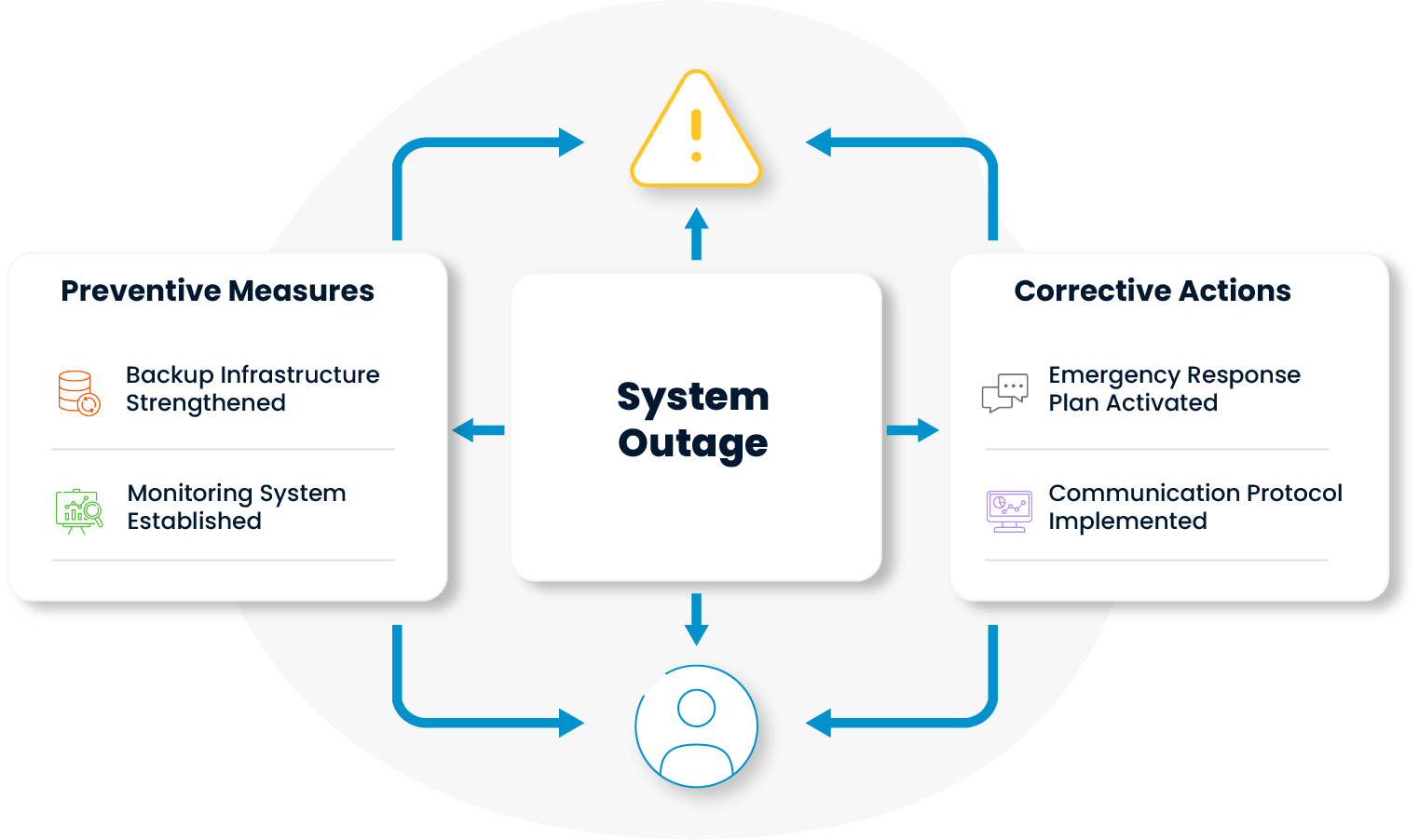
For each risk identified, both preventive measures to be taken before it materializes and corrective actions to be implemented in case the risk materializes are planned. This two-way approach increases both the resilience and recovery capability of organizations.
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
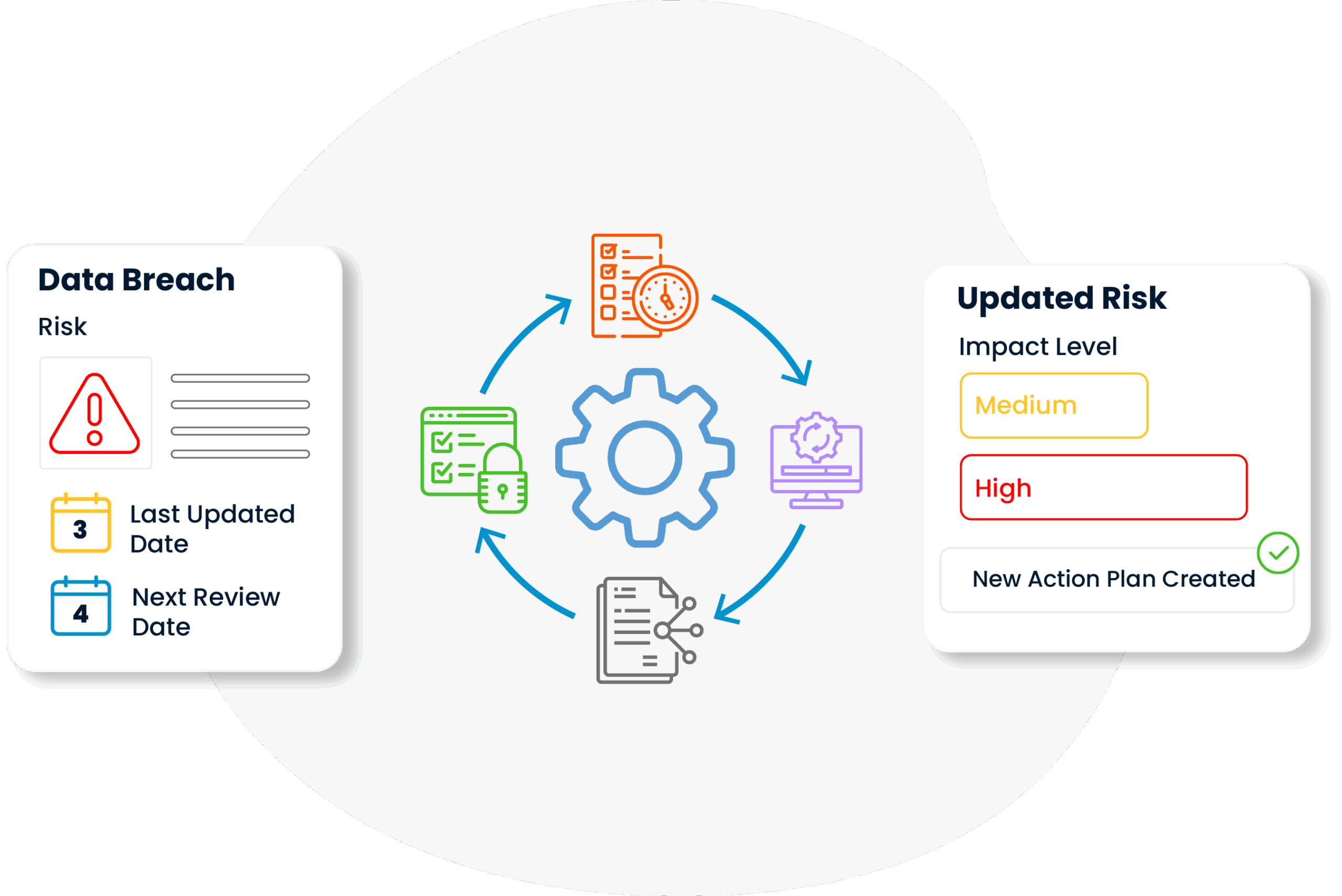
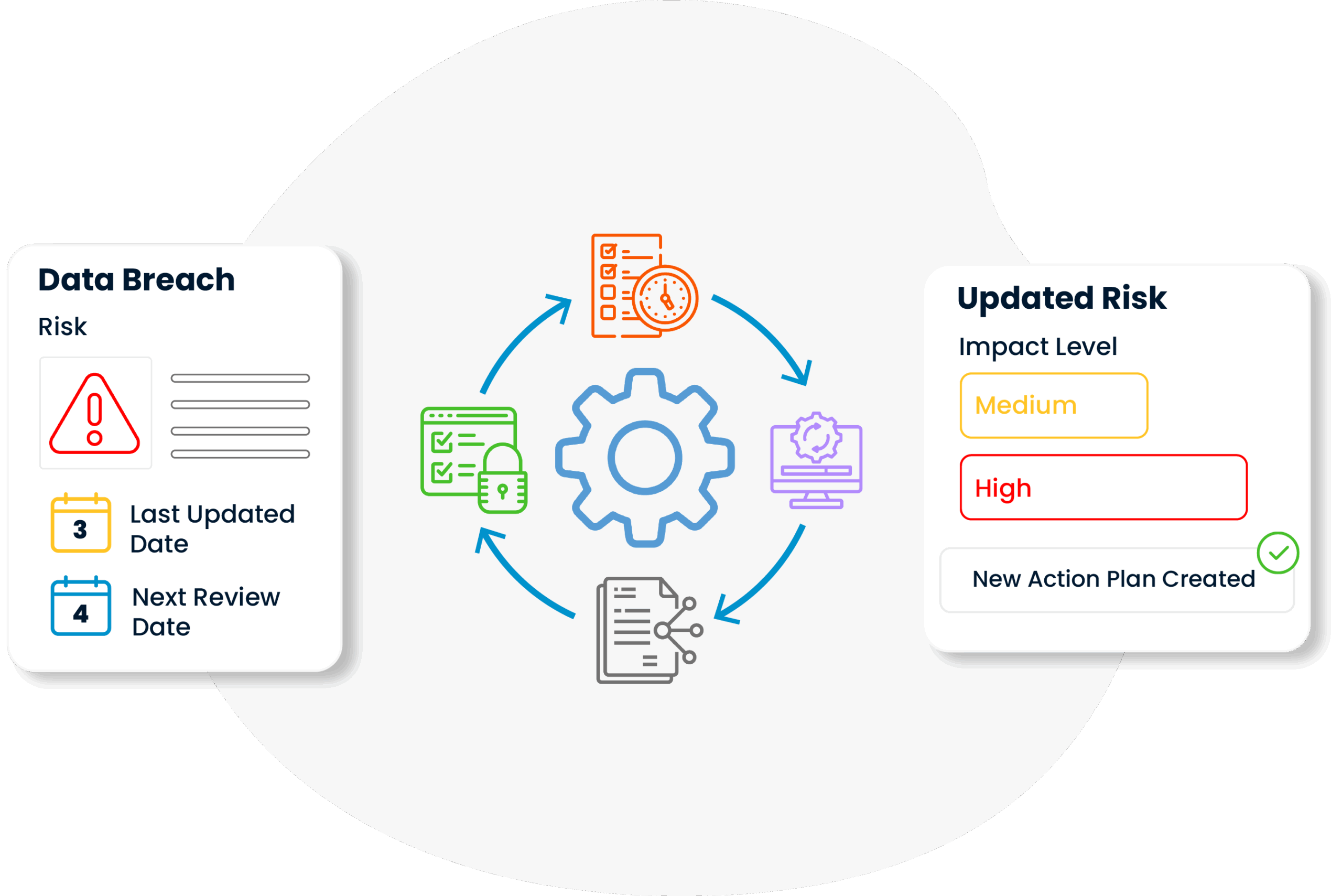
Since risks contain dynamic elements that can change over time, they are not assessed once and left alone; they are reviewed and updated at regular intervals. In this way, the operational security level is always kept up-to-date in line with changes in IT infrastructure or developments in external threat perception.

Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
Warning: Undefined array key "background_image" in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 87
Warning: Trying to access array offset on null in /home/spidya/htdocs/spidya.com/wp-content/plugins/elementor/includes/conditions.php on line 90
In Risk Management practice, all risks, probability analyses, precautions taken and their realizations are systematically documented and turned into reports that can be presented to senior management or audit institutions when necessary. This transparency increases both consistency in internal communication and corporate trust with external stakeholders.

The purpose of Risk Management in IT services is to identify potential risks in advance, mitigate them with effective strategies and ensure uninterrupted continuity of services. Thus, organizations become more resilient in times of crisis and the integrity of the IT infrastructure is ensured.

An effective enterprise risk management approach in IT services supports financial stability by anticipating unexpected costs. Controlling risks in advance optimizes investment and operation costs.

Monitoring the risks identified with Risk Management in IT services and effective control mechanisms prevent IT services from being interrupted. This provides a strong advantage to organizations in terms of service security.

Risk documentation and IT service management processes make it easier for organizations to comply with regulations and audit requirements. This increases credibility in external audits.

Risk analyses guide managers in strategic decision-making processes. Risk-based assessments offer more sustainable results, especially in IT operations management projects.
Features of the Risk Management Module

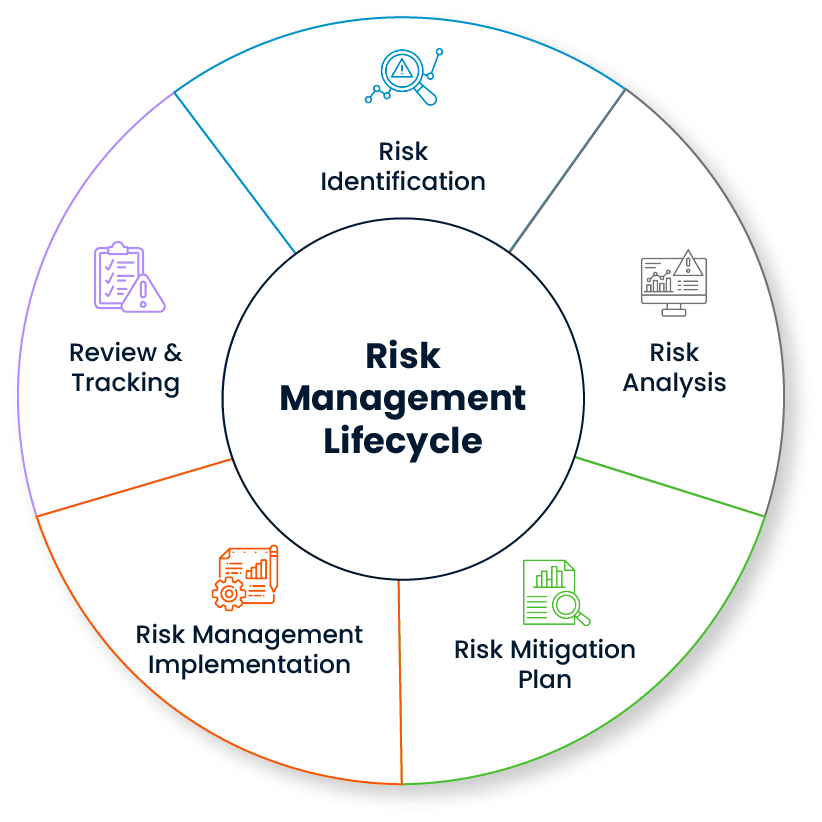
Structured Risk Identification
Risk Assessment Process


Preventive and Corrective Strategies
Continuous Monitoring and Updating

Transparent Documentation and Reporting




Frequently Asked Questions (FAQ)
Early detection of threats in IT service management and IT infrastructure can prevent serious data loss and operational disruptions. Effective risk management not only eliminates instant crises, but also protects digital assets and business continuity so that organizations can confidently achieve their strategic goals. It is therefore a fundamental building block for both security and sustainability.
All IT-related threats such as hardware failures, data breaches, cyber-attacks, workforce losses and service interruptions are included in the risk management process. Thus, all operational threats that the organization may face are addressed with a holistic approach.
No, it is not. Risk management is a critical need for all organizations regardless of scale. Especially Small & Medium Enterprises that rely on digital systems are under threat as much as large corporate structures, and without risk management practices, IT service management business continuity, customer trust and growth plans can be seriously damaged.
Reassessments should be conducted at the start of new projects, changes to existing systems or increased external threat signals. However, conducting an enterprise-wide operational risk management assessment at least once a year ensures that risks are kept up to date and proactive measures are taken.
Risks are usually categorized according to their likelihood (how often could it happen?) and impact (how much damage would it cause if it occurred?). They can also be differentiated according to their source (human, technology, environment) and time of exposure (short-term, long-term). This systematic classification allows organizations to maximize efficiency by directing resources to the most critical risks.
The measures taken in advance for the identified risks eliminate potential vulnerabilities and make the system more resilient. This guarantees the continuity of IT services and contributes to strengthening service security standards in the eyes of both internal and external stakeholders. In the long run, it creates an advantage that directly affects the organization’s reputation and customer trust.
If You Have Any Other Questions, Contact Us!
Early detection of threats in IT service management and IT infrastructure can prevent serious data loss and operational disruptions. Effective risk management not only eliminates instant crises, but also protects digital assets and business continuity so that organizations can confidently achieve their strategic goals. It is therefore a fundamental building block for both security and sustainability.
All IT-related threats such as hardware failures, data breaches, cyber-attacks, workforce losses and service interruptions are included in the risk management process. Thus, all operational threats that the organization may face are addressed with a holistic approach.
No, it is not. Risk management is a critical need for all organizations regardless of scale. Especially Small & Medium Enterprises that rely on digital systems are under threat as much as large corporate structures, and without risk management practices, IT service management business continuity, customer trust and growth plans can be seriously damaged.
Reassessments should be conducted at the start of new projects, changes to existing systems or increased external threat signals. However, conducting an enterprise-wide operational risk management assessment at least once a year ensures that risks are kept up to date and proactive measures are taken.
Risks are usually categorized according to their likelihood (how often could it happen?) and impact (how much damage would it cause if it occurred?). They can also be differentiated according to their source (human, technology, environment) and time of exposure (short-term, long-term). This systematic classification allows organizations to maximize efficiency by directing resources to the most critical risks.
The measures taken in advance for the identified risks eliminate potential vulnerabilities and make the system more resilient. This guarantees the continuity of IT services and contributes to strengthening service security standards in the eyes of both internal and external stakeholders. In the long run, it creates an advantage that directly affects the organization’s reputation and customer trust.
