What Is Network Access Registry?
Network Access Registry (NAR) is a solution framework that discovers devices directly from the network and compares this real-time data with existing IT inventory and CMDB records to identify any discrepancies.
From a technical perspective, Network Access Registry:
Collects MAC addresses, ARP tables, IP addresses, and hostname data directly from network devices.
Normalizes data coming from various sources for consistency.
Deduplicates records to ensure each device is represented only once.
Validates information through a multi-step matching logic.
As a result, Network Access Registry (NAR) is not just a tool that “lists” devices; it is a strategic approach that validates data and generates actionable insights.

Why Network Access Registry Is Vital?
As corporate networks grow, IT teams face one critical question:
‘Which devices are currently active on the network?’
This seemingly simple question points to one of the biggest challenges in modern IT infrastructure. With the constant flux of laptops, IoT devices, cloud services, and remote work tools, tracking every asset and keeping inventory records up to date has become increasingly difficult.
The answer to this complexity lies in an approach that bridges the gap between network reality and inventory records: Network Access Registry (NAR).
In this post, we will explore the challenges of network inventory management, how NAR works, its benefits, and practical implementation examples.
Take Control of Your Future IT Infrastructure Today
Are you ready to eliminate blind spots in your network? To explore solution paths tailored to your organization and learn more about NAR (Network Access Registry), fill out the form and let our experts get in touch with you.
Common Challenges in Enterprise Network Inventory Management
As the number of devices in modern enterprise networks inventory grows every day, tracking them accurately and keeping inventory systems up to date has become a critical challenge. Research shows that, on average, 30% of devices on corporate networks are unregistered. But why is this problem so widespread?
Shadow IT: The Invisible Security Threat
Shadow IT refers to any device connected to the network without the knowledge or approval of the IT department. It could be a smart printer brought from home, an unauthorized IoT gadget, or a server plugged in just for “testing.” Often, none of these appear in your official inventory system.
A Real-World Scenario: In a financial institution, the marketing department purchases an IoT-based customer tracking system and connects it to the office network without IT’s permission. Since this device isn’t subject to firewall rules, it creates a potential gateway for cyberattacks. Yet, because it doesn’t show up in any inventory scans, the security team is completely unaware of the risk.
Inconsistent Inventory Data and Data Silos
Many organizations rely on inventory data from multiple sources: ITSM systems, CMDBs (Configuration Management Databases), network discovery tools, and manual Excel sheets. However, these sources are rarely in sync.
Common Inconsistencies:
A server registered in the CMDB appears with a different IP address during a network scan.
A decommissioned device that has been removed from the network still appears as “active” in the inventory list.
Hostname changes are not updated manually, leading to inaccurate records.
Newly added devices aren’t detected in time, leaving them unregistered and invisible.
The Limitations of Manual Inventory Processes
Many organizations still manage their inventory using Excel spreadsheets, email chains, and manual checks. This approach has significant drawbacks:
High Error Rate: Human error is inevitable.
Poor Data Recency: Information becomes outdated almost instantly.
Labor Intensive: IT teams spend a huge portion of their time on tedious manual tasks.
Scalability Issues: Manual methods collapse as the network grows.
🔴 The consequences of these issues are severe: security vulnerabilities, compliance failures during audits, operational inefficiency, and skyrocketing costs.
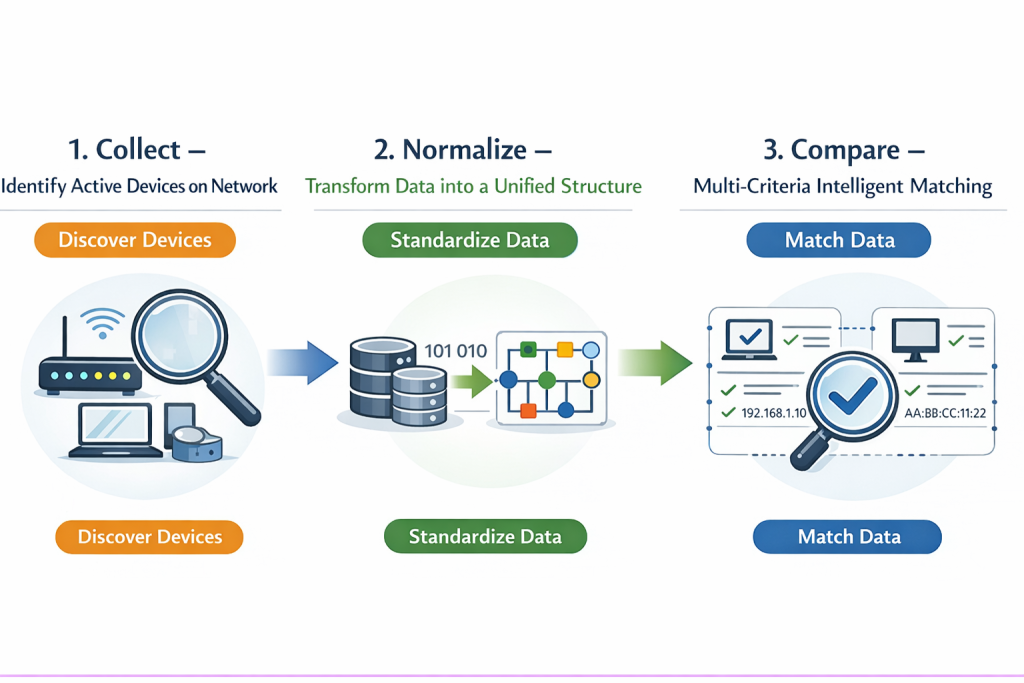
How NAR Works: A 4-Step Operational Framework
Network Access Registry functions through four key phases, each designed to improve data integrity and system precision.
1. Data Collection – Discovering Active Assets on the Network
In the first step, NAR connects to network devices such as switches, routers, and firewalls to automatically collect ARP (Address Resolution Protocol) and MAC address tables. This process identifies the physical presence of every device actually connected to the wire. All major vendors, including Cisco, HP, Huawei, and Juniper, are supported.
Technical Detail: Conducted via the SSH protocol, this collection process can be further enriched with data from Active Directory, DNS records, DHCP server logs, and other authentication systems.
2. Transform – Making Data Speak the Same Language
Data from various sources (CMDB, ITSM, network tools, manual lists) often arrive in different formats. NAR transforms all this information into a common schema—including IP address, MAC address, hostname, device type, source, and timestamp. This normalization process guarantees data consistency across the board.
3. Matching Phase – The Intelligent Decision Engine
This stage is the most critical component of NAR. Every discovered device is processed through a prioritized 3-step matching algorithm:
Step 1 – MAC Address Matching: As the most reliable physical identifier, the MAC address is checked first. If found → MATCHED
Step 2 – Hostname Matching: If no MAC match is found, the system searches by hostname. If found → MATCHED
Step 3 – IP Address Matching: Used as a last resort (lower reliability due to dynamic IPs). If found → CONDITIONALLY MATCHED
If no match is found → UNMATCHED: A new inventory record is automatically created, and a ticket is triggered for the relevant teams.
Consistency Health Checks: For matched records, the system also detects and reports anomalies such as hostname mismatches, IP changes, device type inconsistencies, OS version discrepancies, and “last seen” timeouts.
4. Driving Action – Automated Workflows
This is where NAR delivers its greatest value. Identified inconsistencies don’t just sit in passive reports; they trigger automated actions:
Automatic CMDB Entry Creation: New devices are added with a “Pending Validation” status.
Automated IT Ticketing: Tickets are opened for IT teams based on a predefined priority matrix.
Detailed Reporting & Dashboards: Real-time visibility through instant updates.
Seamless Integration: REST API support for popular ITSM systems like ServiceNow and Jira Service Management.
Network Access Registry: Strategic Benefits for Organizations
NAR transforms inventory tracking from a burden into a security and efficiency shield for your IT operations.
1. Security and Risk Management
Shadow IT Visibility: Identify every device connecting to the network instantly and block unauthorized access within seconds.
Rapid Incident Response: Manage crises effectively by immediately identifying device ownership and physical location during an attack.
Case Study: In a healthcare organization, NAR enabled the detection and blocking of an unauthorized device in under 3 minutes.
2. Audit and Regulatory Compliance
Always Audit-Ready: Automatically generate reports required for KVKK, ISO 27001, and BDDK without the hassle of manual work.
95%+ Inventory Accuracy: Eliminate human error and ensure your CMDB records are always up to date.
3. Operational Efficiency and ROI
70% Time Savings: Automate the manual inventory process and save your team up to 240 hours per year.
Cost Optimization: Prevent budget waste by identifying unused licenses and dormant hardware.
Network Access Registry: Industry Use Cases
🏦 Finance: The Power of Regulation and Audit
The Problem: An error-prone, manual inventory process across 50+ branches, leaving the organization unprepared for BDDK audits.
The NAR Solution: Automated data collection from branch network devices combined with Active Directory integration.
The Impact: Inventory accuracy soared to 96%; ISO 27001 and BDDK-compliant reports are now generated with a single click.
🏥 Healthcare: Medical IoT Security
The Problem: Inability to track hundreds of network-connected MRI machines, ultrasounds, and patient monitors, creating significant security gaps.
The NAR Solution: Auto Network Discovery of all medical devices and audit of firewall rule compliance.
The Impact: Patient data security was fortified; firmware updates were successfully automated.
🚀 E-Commerce: Dynamic Scalability
The Problem: The impossible task of manually tracking dozens of new servers added every month.
The NAR Solution: A unified, real-time view of both cloud and on-premise infrastructure.
The Impact: DevOps teams received real-time data feeds; not a single device remained unregistered despite rapid growth.
Common Misconceptions About NAR
Let’s be clear: What does NAR actually do—and what does it not?
It’s Not an ITSM/CMDB Killer: It doesn’t replace your existing systems; instead, it empowers them by feeding them accurate, real-time data.
It’s Not a Firewall: It doesn’t block devices on its own; it identifies and reports every asset on the network, leaving the final decision to you.
It’s Not a Performance Monitor: It doesn’t measure bandwidth or speed; its focus is entirely on device presence and ownership.
It’s Not Vendor-Locked: It is compatible with various manufacturers like Cisco, HP, and Huawei; it operates as an ecosystem-independent solution.
NAR Success Scorecard: How Do We Measure Performance? (KPIs)
Track the success of your NAR investment with tangible data:
Accuracy Rate: The match rate between inventory data and reality (Target: 95%+).
Discovery Speed: The time it takes for a new device to appear on the radar (Target: <15 min).
Shadow IT Detection: The percentage of unregistered devices successfully identified.
Operational Gain: The reduction in manual hours spent on inventory management.
Conclusion: From Static Lists to Dynamic Management
In today’s world, a network inventory is not just a “file”—it is a living, breathing process. Network Access Registry (NAR) accepts your network as the single Source of Truth and keeps it up-to-date at every moment.
Clear Gains with NAR:
Proactive Security: You cannot control what you cannot see; gain full visibility of every endpoint with NAR.
Regulatory Compliance: Leave no room for surprises during audits.
Maximum Efficiency: Free your team from manual tasks and allow them to focus on innovation.